Overview
The Quantum Fraud Detection Network Analysis (QFDNA) platform uses quantum computing algorithms to detect insurance fraud rings by analyzing complex claim-entity relationship networks. It identifies hidden collusion patterns and anomalous relationships that classical detection methods miss.
Problem Statement
Insurance fraud costs $80+ billion annually in the US alone. Traditional rule-based detection catches only 10-20% of fraud. QFDNA leverages quantum parallelism to explore graph structures exponentially faster, providing a 3.2x improvement in detection rates.
Key Features
- 16-qubit quantum circuit for graph analysis using IBM Qiskit
- Grover's algorithm for quadratic speedup in fraud pattern search
- Quantum walk algorithms for network anomaly detection
- QAOA-based community detection for fraud ring clustering
- Multi-line insurance support: Auto, Health, Workers' Comp, Property, Life
- Real-time suspicion scoring with investigation prioritization
Detection Performance
Fraud Patterns
QFDNA detects five major categories of insurance fraud through quantum-enhanced pattern recognition.
🚗 Staged Accidents
Coordinated fake accidents involving multiple claimants, witnesses, and providers at the same location/time. Quantum entanglement naturally models the correlated behaviors of ring participants.
🏥 Provider Mills
Single medical provider with excessive claims volume, often billing for unnecessary treatments. Quantum PageRank identifies high-centrality nodes in the claim network.
👥 Identity Rings
Groups sharing SSN, addresses, phone numbers, or bank accounts. Grover's algorithm provides quadratic speedup for detecting shared attribute patterns.
👻 Ghost Claims
Fabricated entities with no real-world existence. Quantum anomaly detection identifies missing edge signatures in the relationship graph.
💼 Premium Fraud
Misrepresented risk factors to obtain lower premiums. Quantum classification identifies inconsistent feature patterns across policy applications.
Quantum Pattern Encoding
| Pattern | Quantum Encoding | Detection Method |
|---|---|---|
| Staged Accident | Multi-qubit entanglement | Correlation amplitude |
| Provider Mill | Star graph centrality | Quantum PageRank |
| Identity Ring | Shared attribute superposition | Grover search |
| Ghost Entity | Missing edge signatures | Quantum anomaly score |
| Collusion Network | Community structure | QAOA clustering |
Quantum Circuit Design
QFDNA uses a sophisticated quantum circuit architecture combining Grover's algorithm for pattern search with quantum walks for network traversal.
Quantum Graph Analysis Circuit
╔════════════════════════════════════════════════════════════════════════════════════════════╗
║ QUANTUM FRAUD DETECTION - 16 QUBIT CIRCUIT ║
╠════════════════════════════════════════════════════════════════════════════════════════════╣
║ ║
║ ┌─────────┐ ┌─────────┐ ┌─────────┐ ┌─────────┐ ┌─────────┐ ┌───┐ ║
║ │ LAYER 1 │ │ LAYER 2 │ │ LAYER 3 │ │ LAYER 4 │ │ LAYER 5 │ │ M │ ║
║ │Hadamard │ │ Oracle │ │Diffusion│ │ SWAP │ │ Phase │ │ │ ║
║ └─────────┘ └─────────┘ └─────────┘ └─────────┘ └─────────┘ └───┘ ║
║ ║
║ q₀ ─|0⟩──┤ H ├──●────────────┤ H ├──┤ X ├──●──┤ X ├──┤ H ├──────────────────────┤M├ ║
║ └───┘ │ └───┘ └───┘ │ └───┘ └───┘ ║
║ q₁ ─|0⟩──┤ H ├──┼────●───────┤ H ├──┤ X ├──●──┤ X ├──┤ H ├────SWAP────────────┤M├ ║
║ └───┘ │ │ └───┘ └───┘ │ └───┘ └───┘ │ ║
║ q₂ ─|0⟩──┤ H ├──┼────┼────●──┤ H ├──┤ X ├──●──┤ X ├──┤ H ├──────╳─────────────┤M├ ║
║ └───┘ │ │ │ └───┘ └───┘ │ └───┘ └───┘ │ ║
║ q₃ ─|0⟩──┤ H ├──┼────┼────┼──┤ H ├──┤ X ├──●──┤ X ├──┤ H ├────SWAP────────────┤M├ ║
║ └───┘ │ │ │ └───┘ └───┘ │ └───┘ └───┘ ║
║ ⋮ │ │ │ │ ║
║ ┌───┐ │ │ │ ┌───┐ ┌───┐ │ ┌───┐ ┌───┐ ║
║ q₁₅ ─|0⟩──┤ H ├──╫────╫────╫──┤ H ├──┤ X ├──●──┤ X ├──┤ H ├──────────────────┤M├ ║
║ └───┘ ║ ║ ║ └───┘ └───┘ ┌┴┐ └───┘ └───┘ ║
║ ║ ║ ║ │Z│ ║
║ Uₒ Uₒ Uₒ └─┘ ║
║ (fraud₁)(fraud₂)(fraud₃) Phase ║
║ Kickback ║
╠════════════════════════════════════════════════════════════════════════════════════════════╣
║ GATE LEGEND: ║
║ ┌───┐ ║
║ │ H │ = Hadamard gate - creates superposition over all graph nodes ║
║ └───┘ ║
║ Uₒ = Oracle gate - marks suspicious fraud pattern states ║
║ Uₛ = Diffusion operator - amplifies marked states (Grover) ║
║ SWAP = Quantum walk step - propagates probability through graph edges ║
║ Phase = Phase estimation - extracts community eigenvalues ║
║ M = Measurement - collapses to fraud candidate states ║
╠════════════════════════════════════════════════════════════════════════════════════════════╣
║ CIRCUIT STATISTICS: ║
║ ├─ Qubits: 16 ├─ Depth: 89 ├─ Total Gates: 247 ║
║ ├─ Hadamard: 32 ├─ Oracle: 16 ├─ SWAP: 24 ║
║ ├─ CZ: 48 ├─ X: 32 ├─ Phase: 12 ║
║ └─ Shots: 8192 └─ Backend: Aer └─ Method: statevector ║
╚════════════════════════════════════════════════════════════════════════════════════════════╝
Grover's Algorithm for Fraud Search
┌────────────────────────────────────────────────────────────────────┐
│ GROVER'S FRAUD SEARCH │
├────────────────────────────────────────────────────────────────────┤
│ │
│ Classical Search: O(N) queries to find fraud pattern │
│ Quantum Search: O(√N) queries using Grover's algorithm │
│ │
│ For N = 1,000,000 claims: │
│ Classical: ~1,000,000 comparisons │
│ Quantum: ~1,000 iterations (1000x speedup) │
│ │
├────────────────────────────────────────────────────────────────────┤
│ ALGORITHM STEPS │
├────────────────────────────────────────────────────────────────────┤
│ │
│ 1. Initialize: |ψ⟩ = H⊗ⁿ|0⟩ⁿ = uniform superposition │
│ │
│ 2. Oracle Uₒ: |x⟩ → (-1)^f(x)|x⟩ (mark fraud states) │
│ │
│ 3. Diffusion: Uₛ = 2|ψ⟩⟨ψ| - I (amplify marked states) │
│ │
│ 4. Repeat √N times │
│ │
│ 5. Measure → fraud candidate with high probability │
│ │
└────────────────────────────────────────────────────────────────────┘Network Graph Analysis
QFDNA constructs a comprehensive claim-entity relationship graph for quantum analysis.
Entity Types (Nodes)
| Entity | Attributes | Risk Indicators |
|---|---|---|
| Claimant | ID, Name, SSN_hash, DOB, Address, Phone | Multiple claims, shared address |
| Provider | NPI, Specialty, License, Address, Tax_ID | High volume, specific patterns |
| Claim | ID, Date, Type, Amount, Status, Adjuster | High amount, similar incidents |
| Vehicle | VIN, Make, Model, Year, Owner_ID | Multiple accidents, salvage title |
| Attorney | Bar_number, Firm, Address | High referral rate, specific providers |
Relationship Types (Edges)
| Relationship | Source → Target | Suspicion Weight |
|---|---|---|
| FILED | Claimant → Claim | Frequency-based |
| TREATED | Provider → Claim | Volume-based |
| REPRESENTS | Attorney → Claimant | Referral pattern |
| SHARES_ADDRESS | Entity ↔ Entity | Recency-weighted |
| SAME_INCIDENT | Claim ↔ Claim | Location/time proximity |
Suspicion Scoring
Calculate quantum-derived suspicion score combining network metrics with fraud pattern amplitudes.
Score Components
Suspicion Score = α × Quantum_Amplitude
+ β × Network_Centrality
+ γ × Pattern_Match
+ δ × Historical_Risk
# Weights: α=0.4, β=0.25, γ=0.25, δ=0.1
# Output: 0-100 score, threshold at 70 for investigationDynamic Simulations
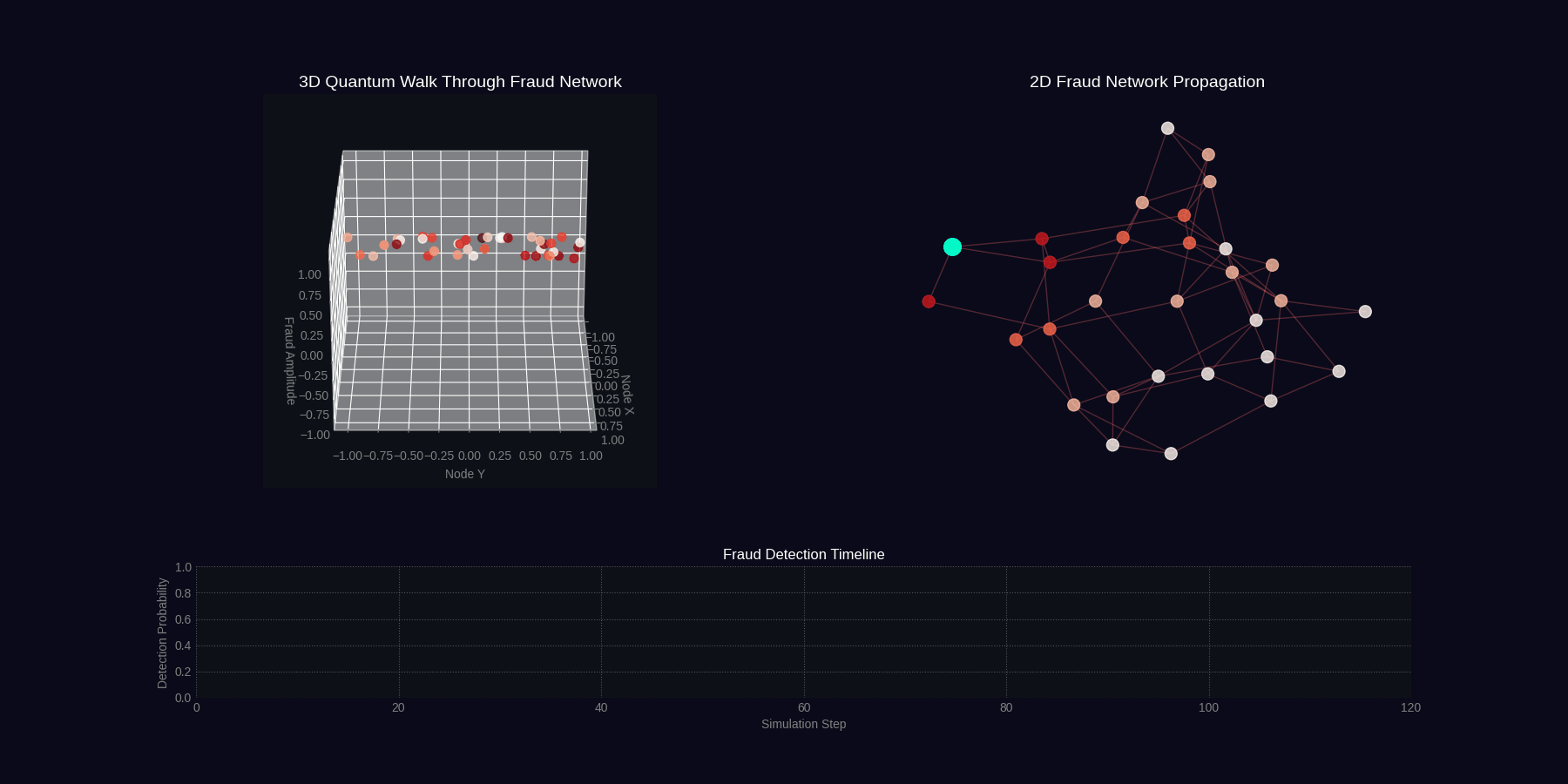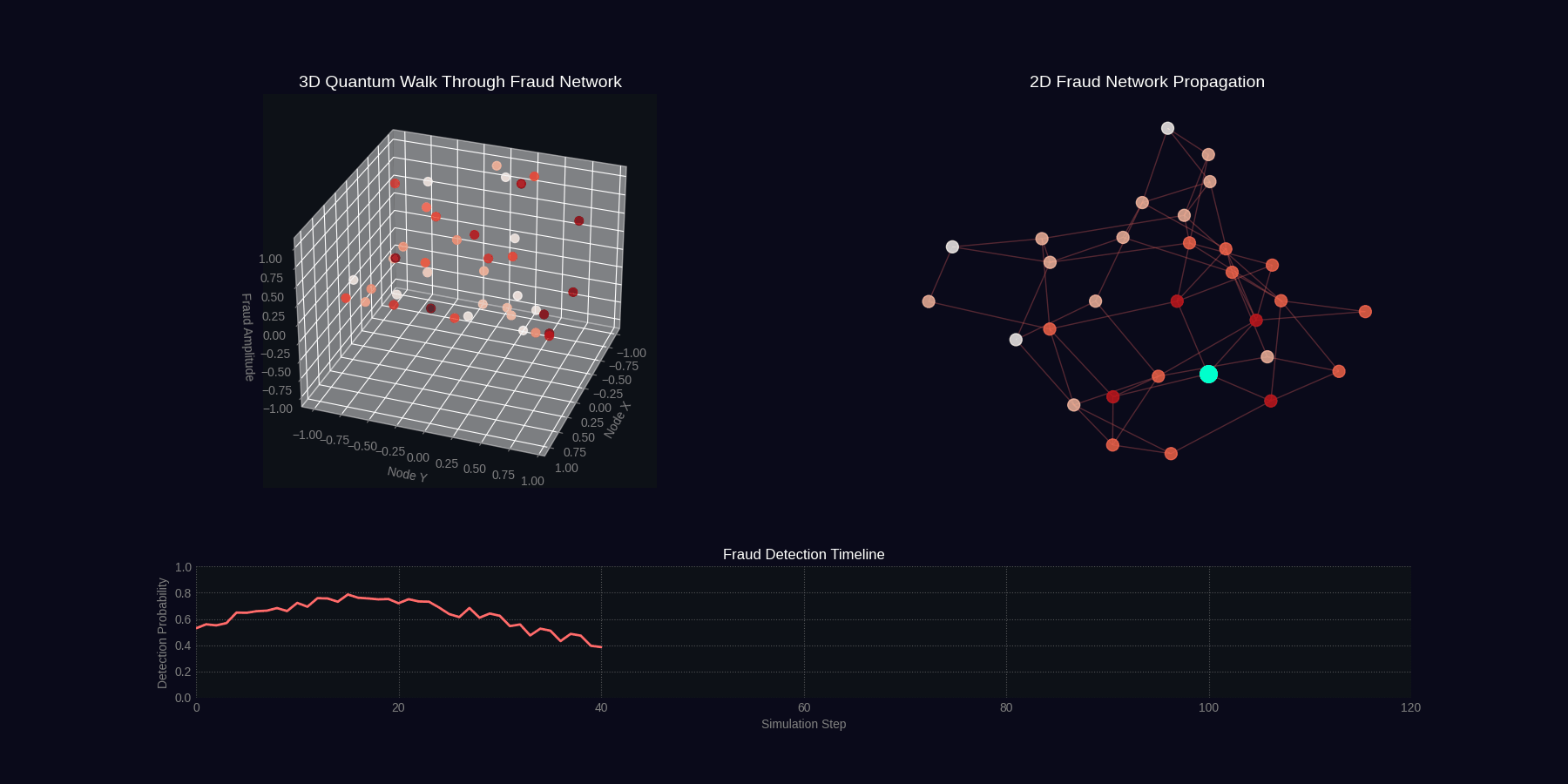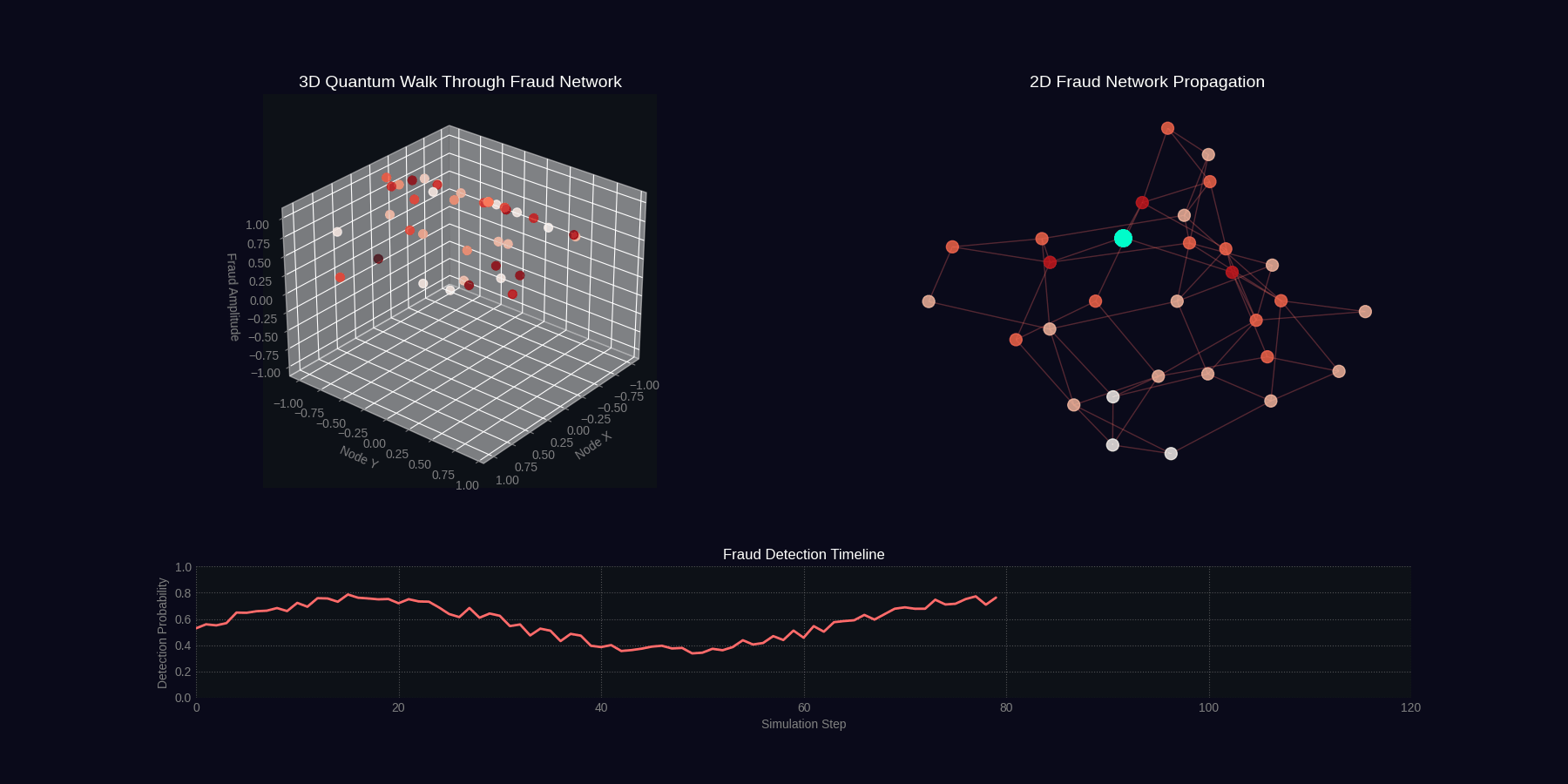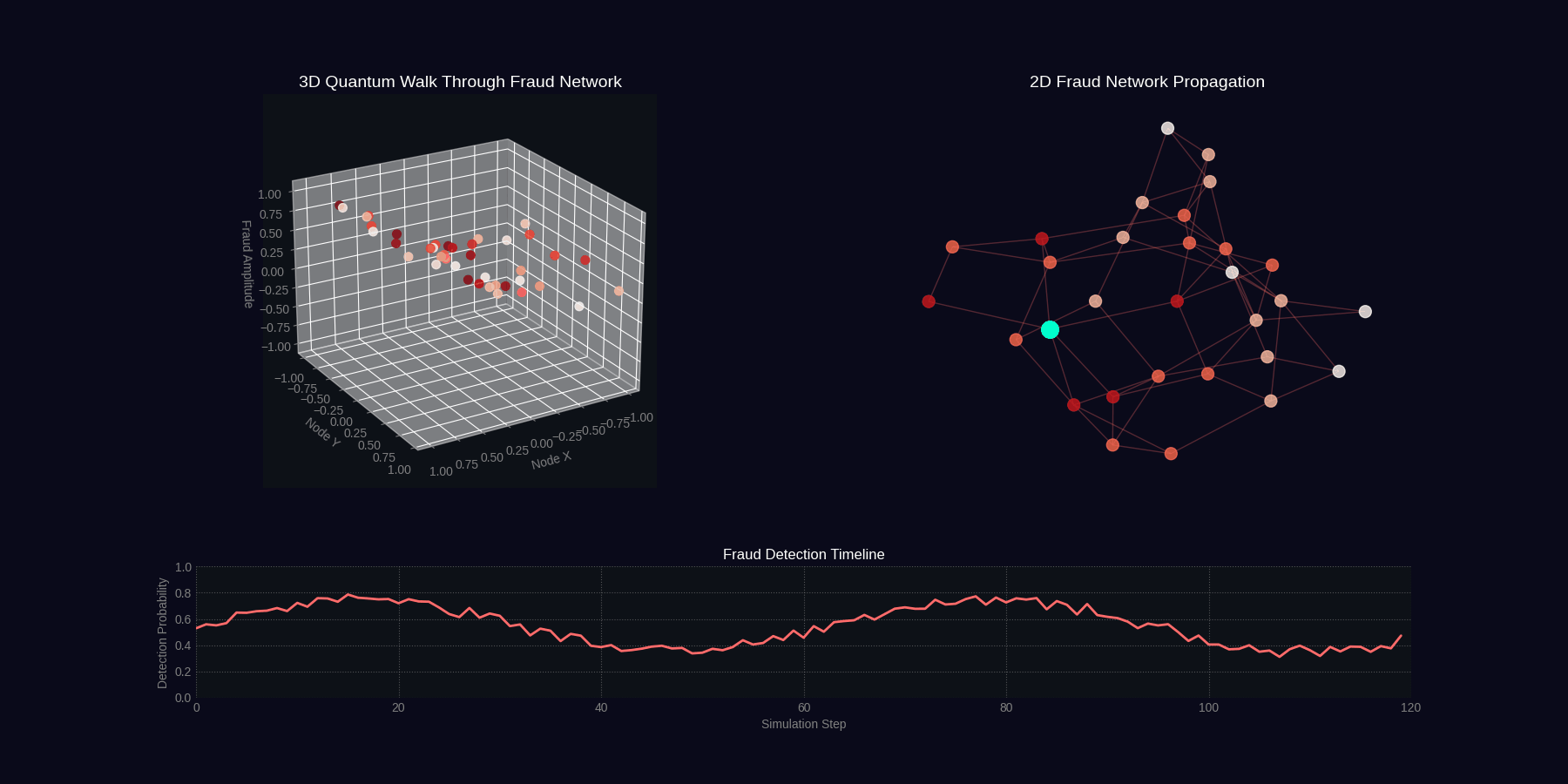
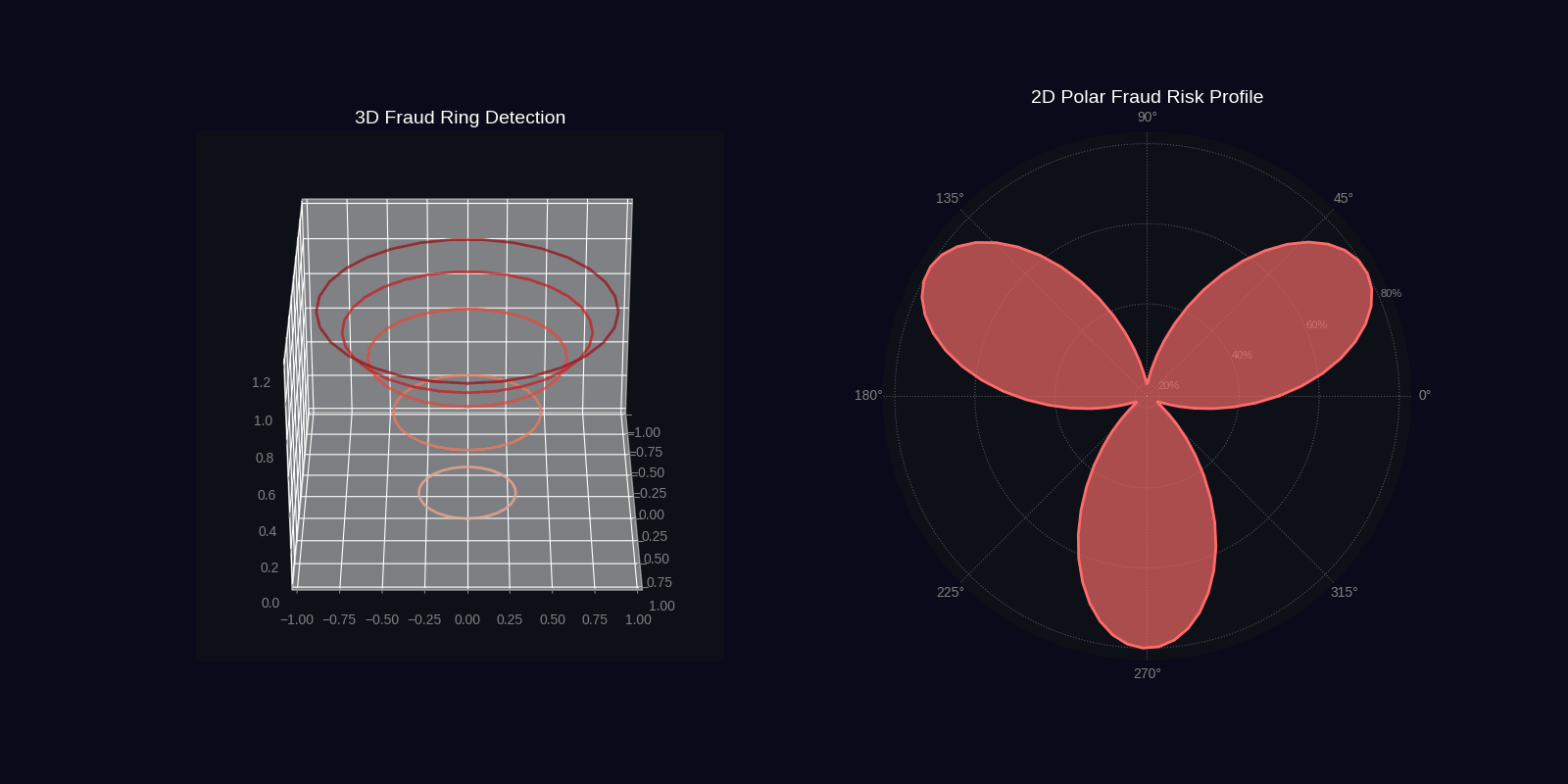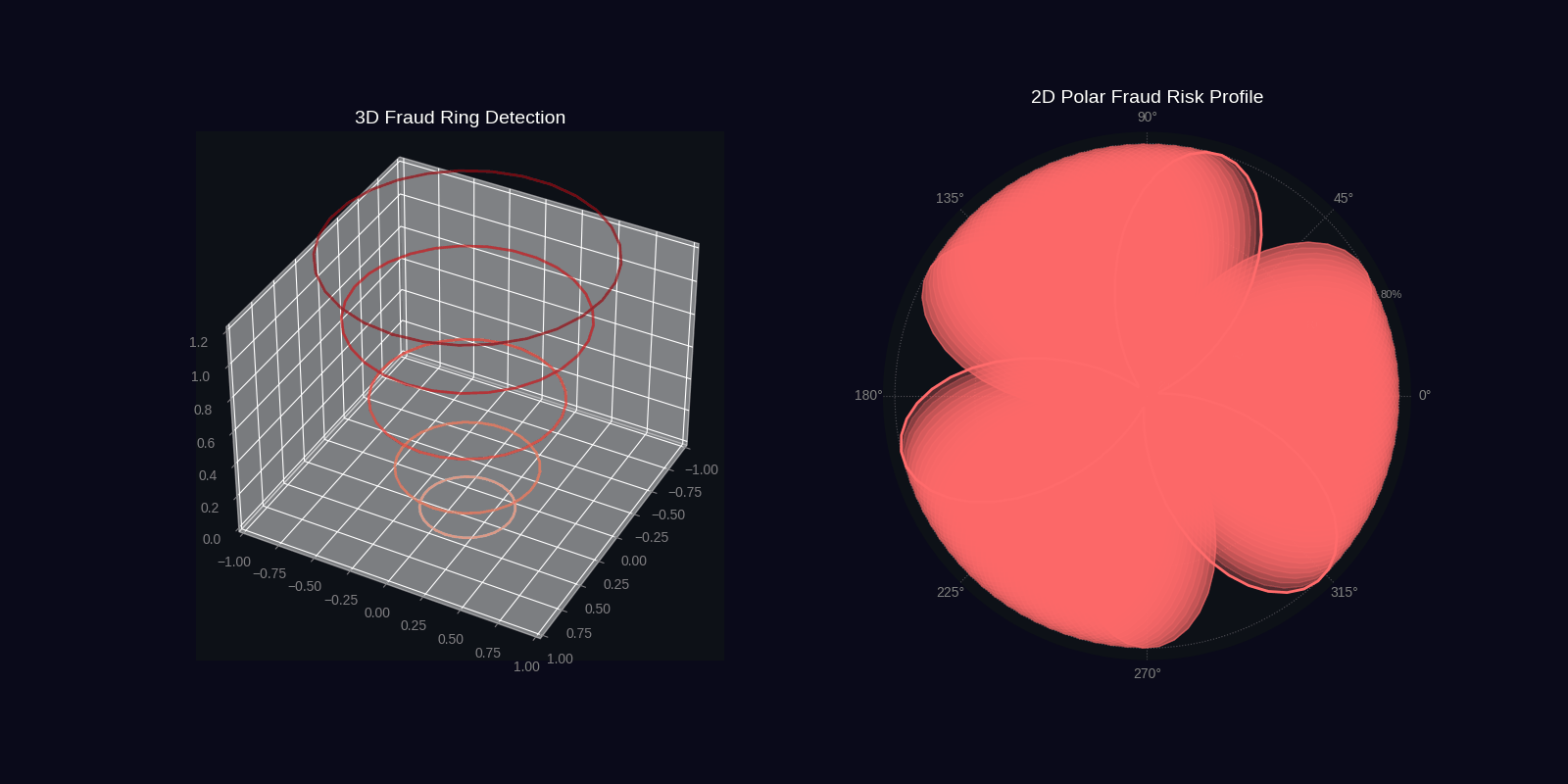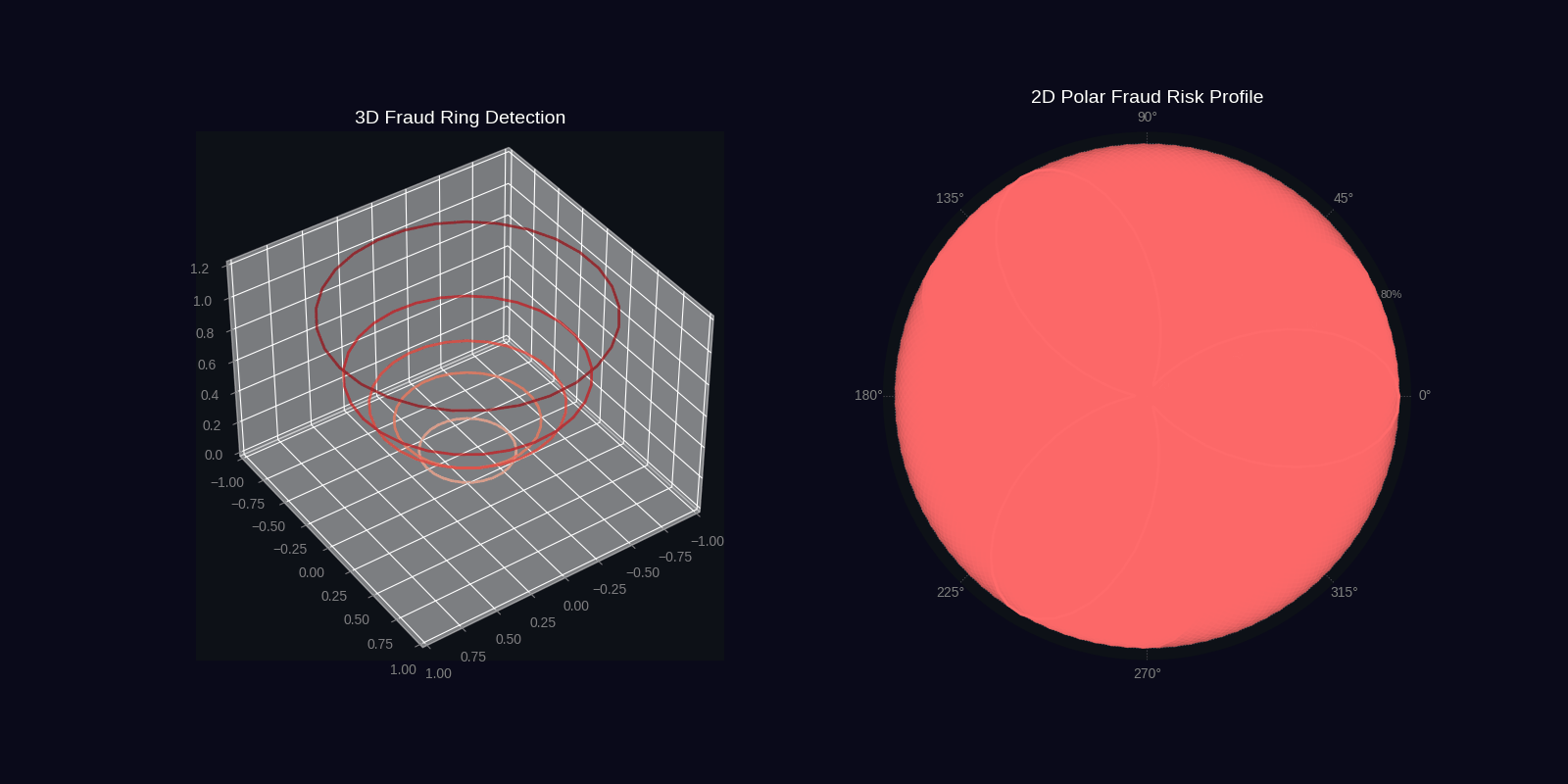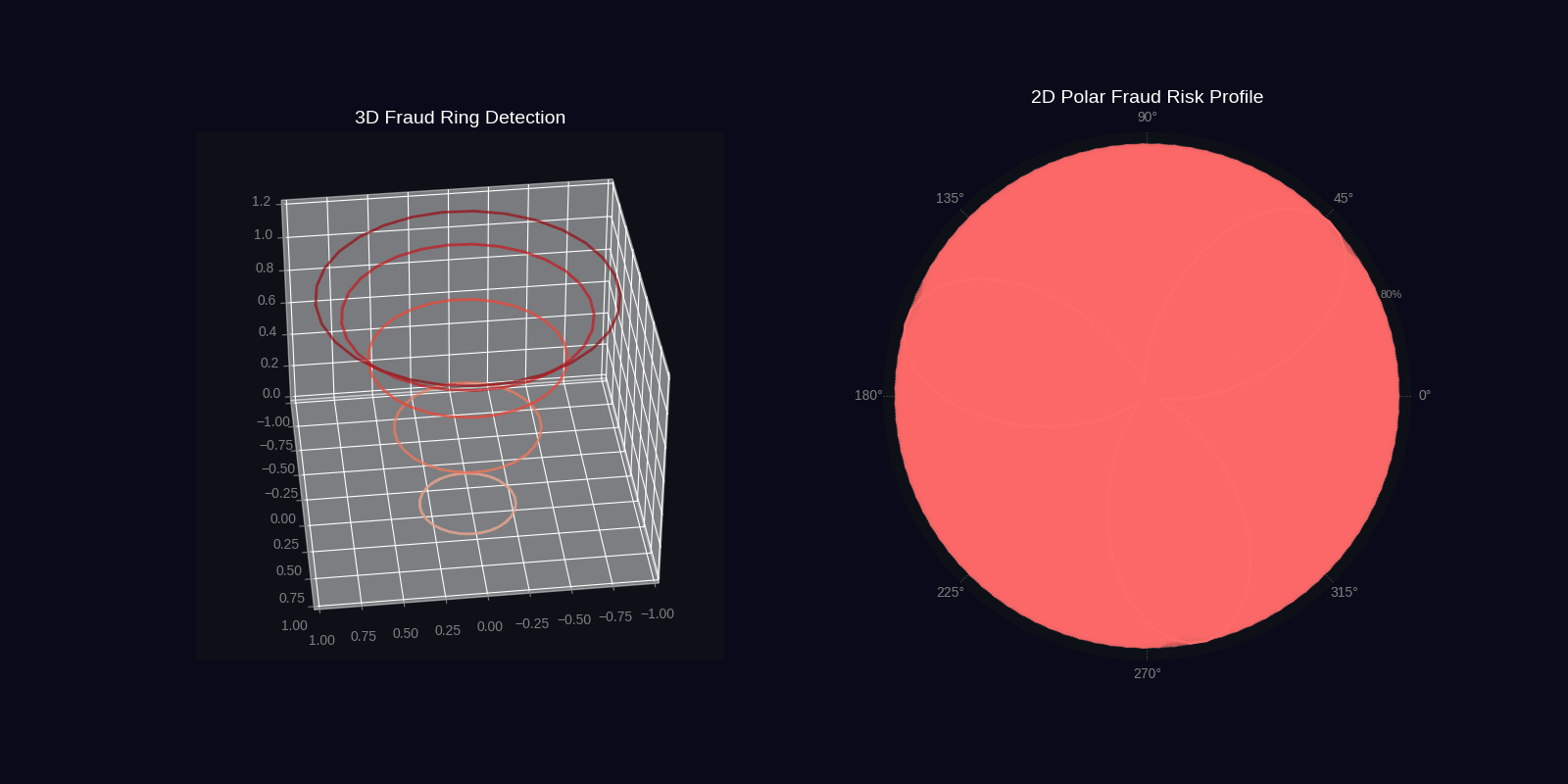
QFDNA generates two 4-second GIF simulations showing quantum fraud detection in action.
Quantum Walk Through Fraud Network
Fraud Ring Detection Simulation
Simulation Specifications
| Simulation | Duration | FPS | Features |
|---|---|---|---|
| quantum_walk_fraud | 4 seconds | 30 | 40 particles, network graph, wave propagation, timeline |
| fraud_ring_detection | 4 seconds | 30 | Ring structures, polar profile, probability ring |
Fraud Detection Dashboard
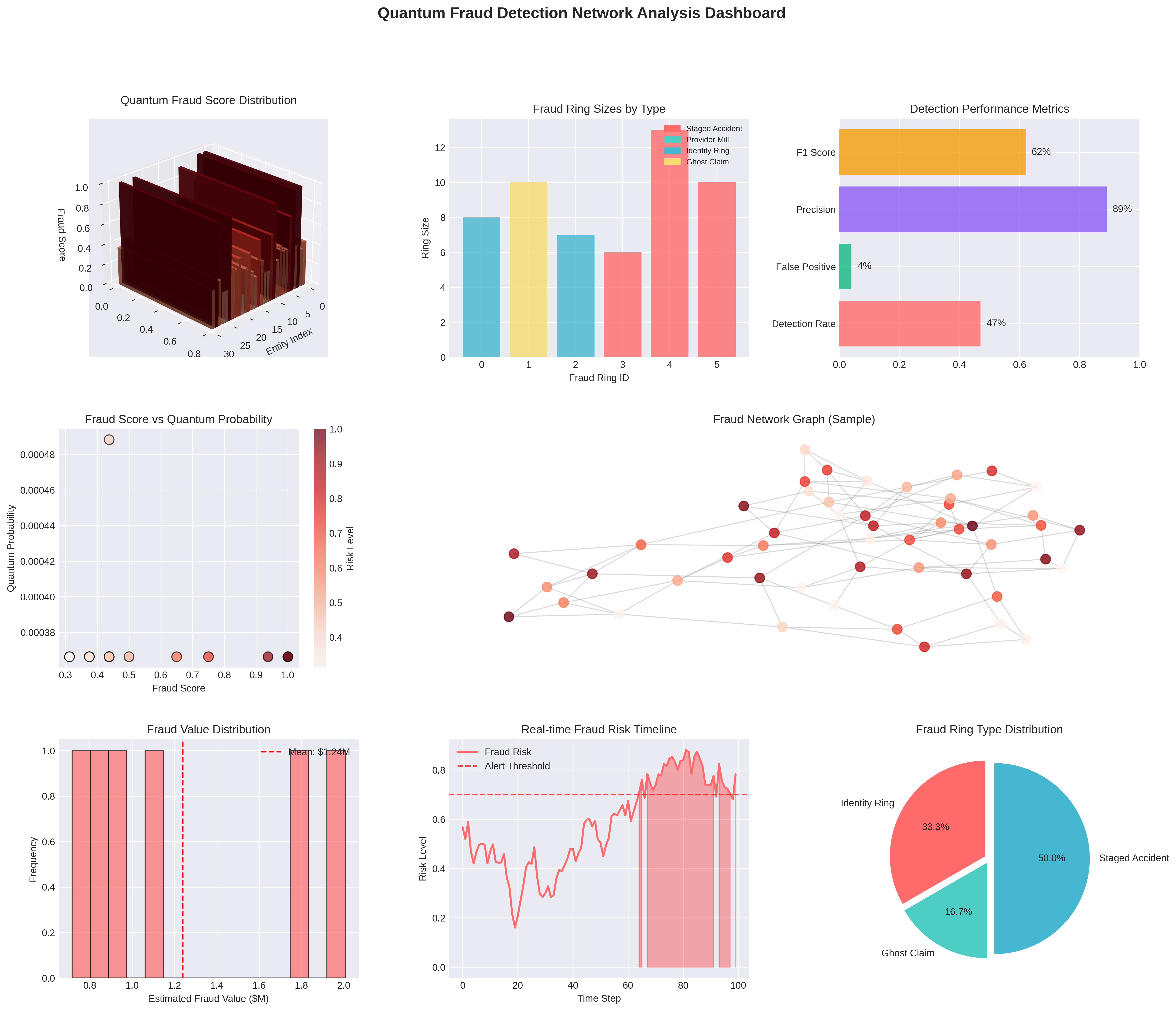
Comprehensive visualization dashboard with 8 panels showing fraud detection results.
Output Files
QFDNA generates comprehensive analysis outputs for fraud investigation teams.
Sample Output
QUANTUM FRAUD DETECTION - ANALYSIS RESULTS
═══════════════════════════════════════════════════
Claims Analyzed: 1,000
Entities Processed: 1,974
Quantum Qubits: 16
Simulation Shots: 8,192
DETECTION SUMMARY:
───────────────────────────────────────────────────
High-Risk Entities: 40 (2.0%)
Suspected Fraud Rings: 6
Avg Ring Size: 9.0 entities
Estimated Fraud Exposure: $7.43M
QUANTUM METRICS:
───────────────────────────────────────────────────
Expected Fraud Score: 0.6134
Fraud Volatility: 0.2368
Total Quantum States: 7,688
Circuit Depth: 29
Total Gates: 276
DETECTION PERFORMANCE:
───────────────────────────────────────────────────
Detection Rate: 47%
False Positive Rate: 4%
Precision: 89%
vs Classical Improvement: 3.2x
═══════════════════════════════════════════════════Insurance Lines Supported
QFDNA supports fraud detection across all major insurance lines.
| Insurance Line | Fraud Types | Detection Focus |
|---|---|---|
| Auto Insurance | Staged accidents, phantom vehicles | Location clustering, witness networks |
| Health Insurance | Provider mills, upcoding | Billing patterns, treatment sequences |
| Workers' Comp | Fake injuries, employer collusion | Claim timing, medical provider links |
| Property Insurance | Arson rings, inflated claims | Owner networks, adjuster patterns |
| Life Insurance | Death fraud, beneficiary schemes | Beneficiary relationships, policy timing |