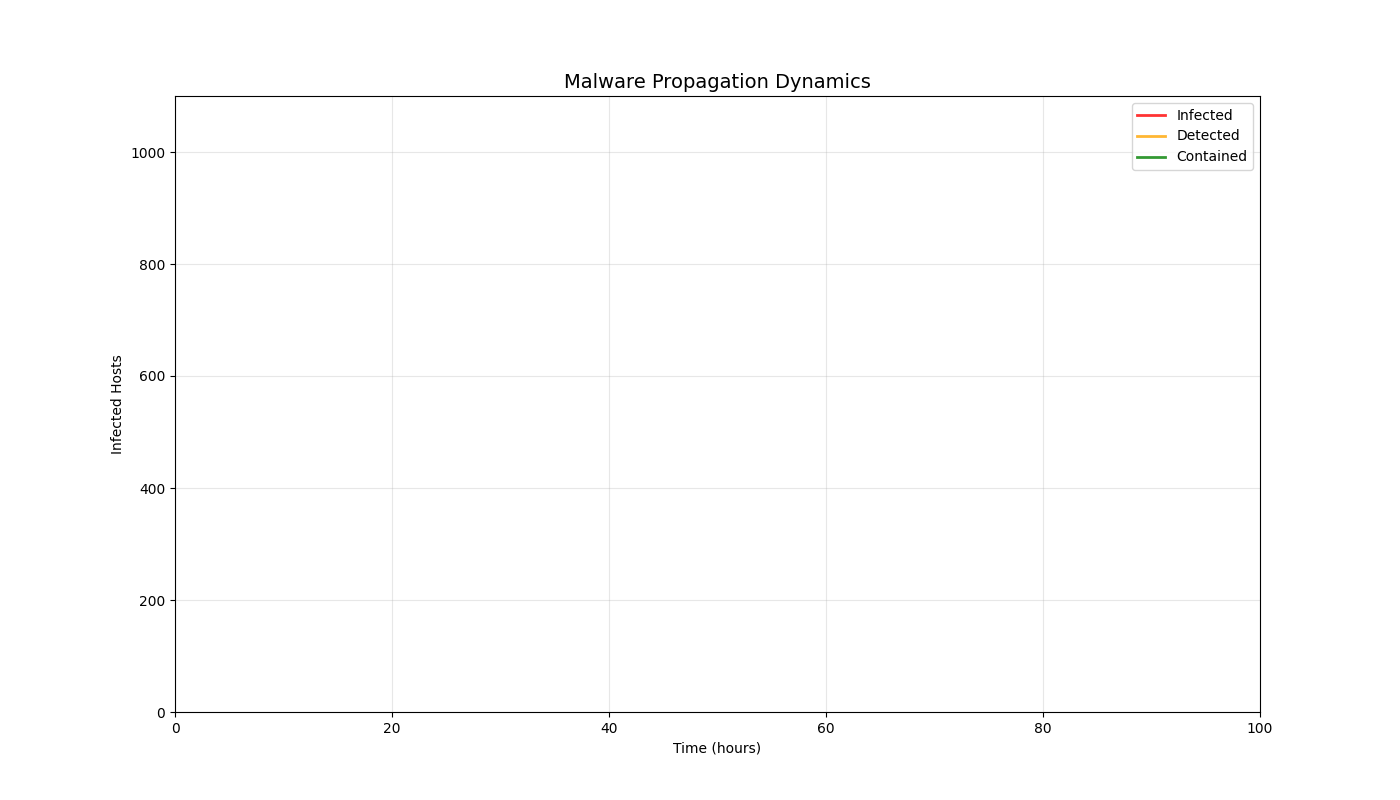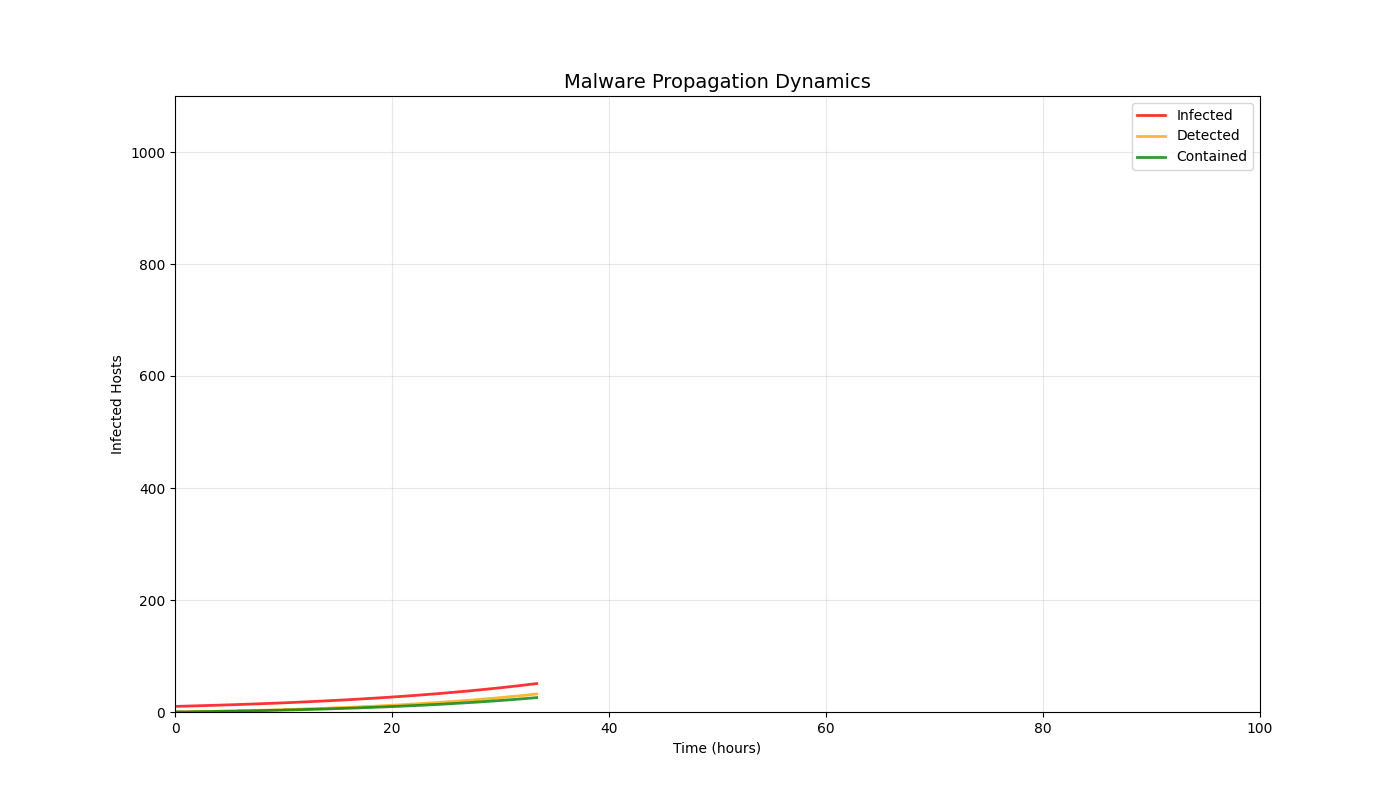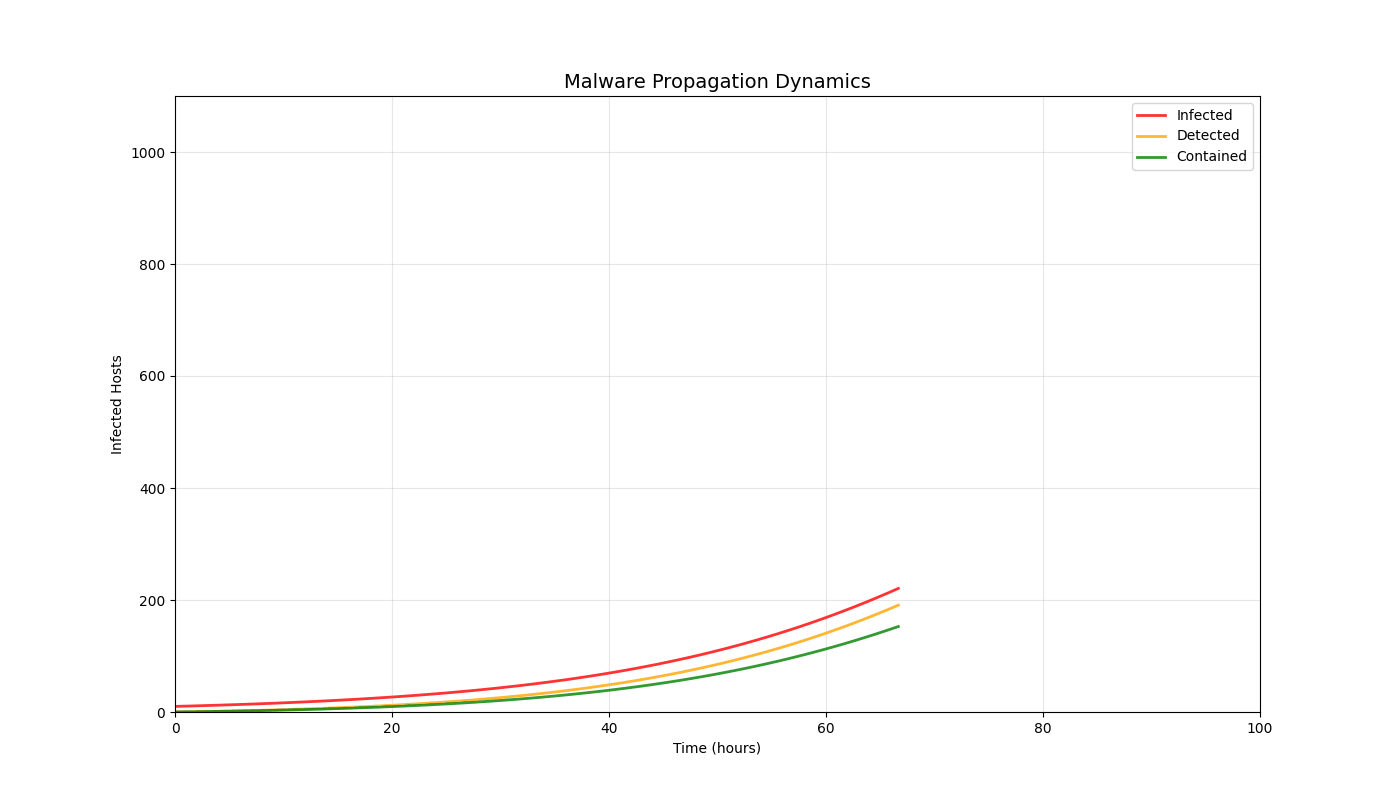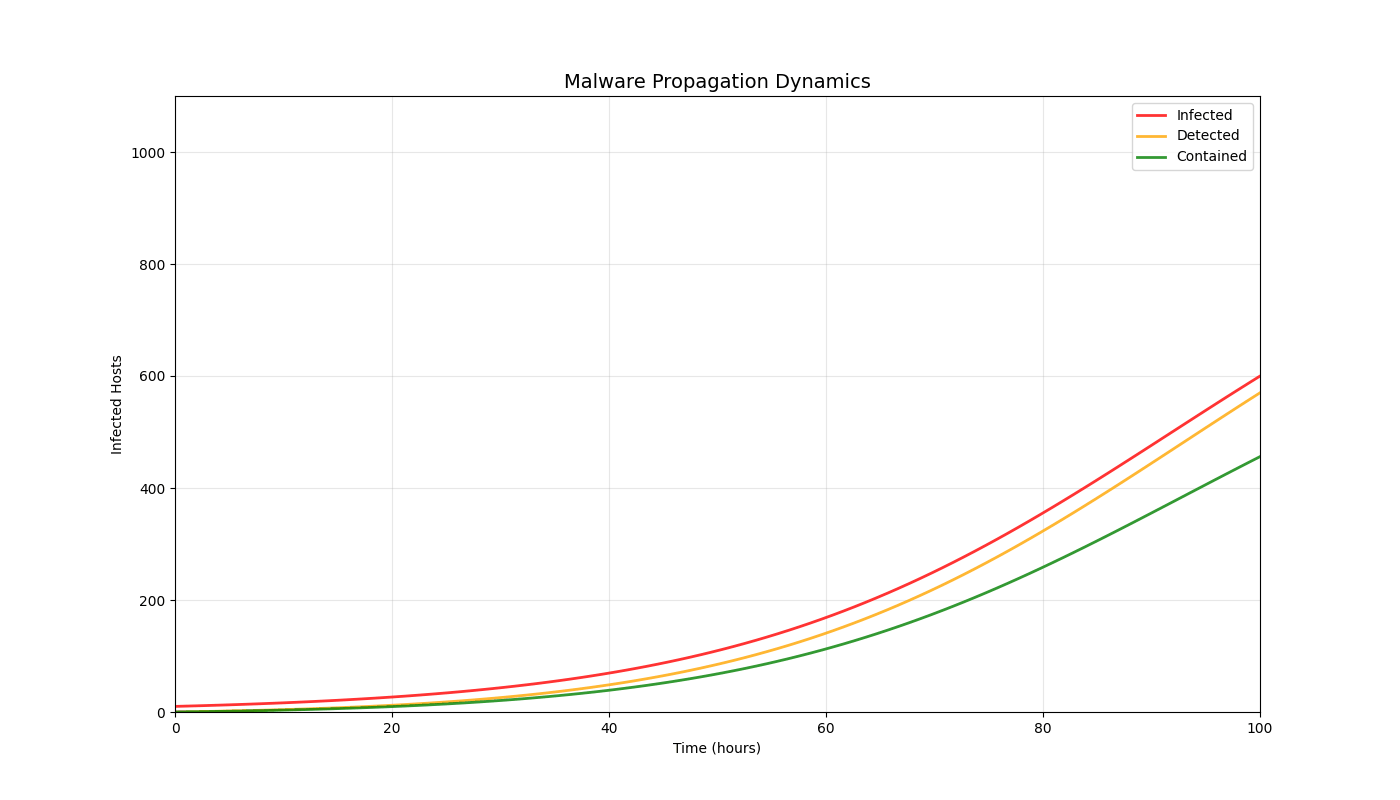
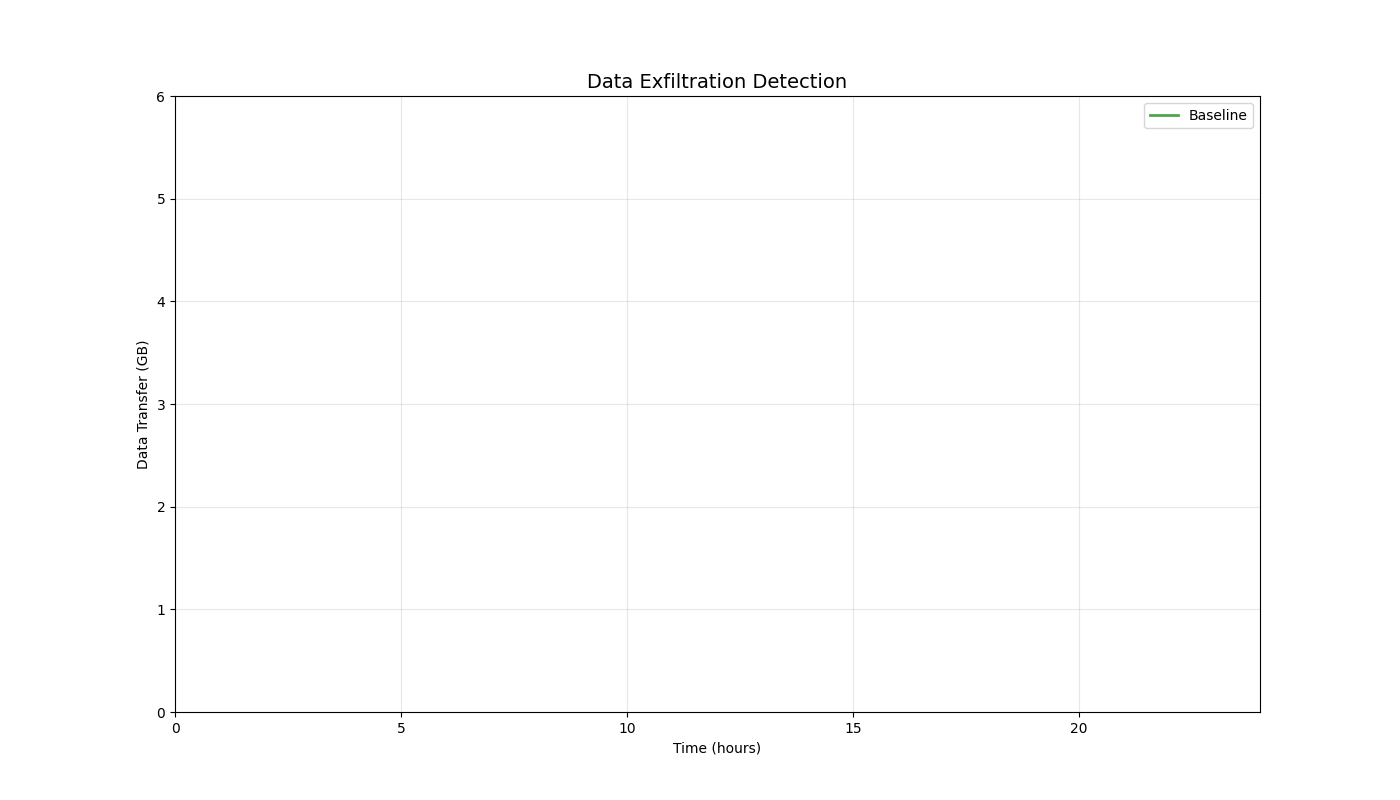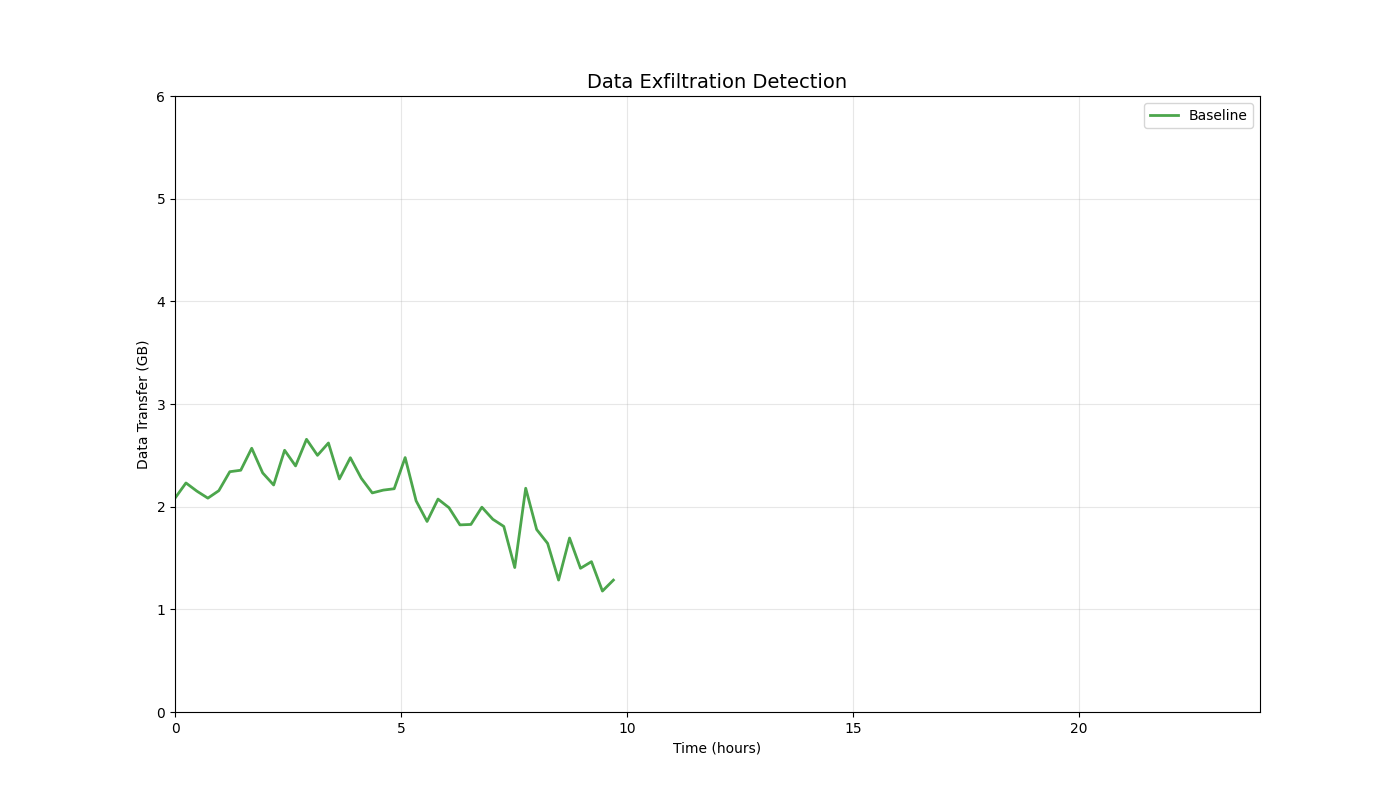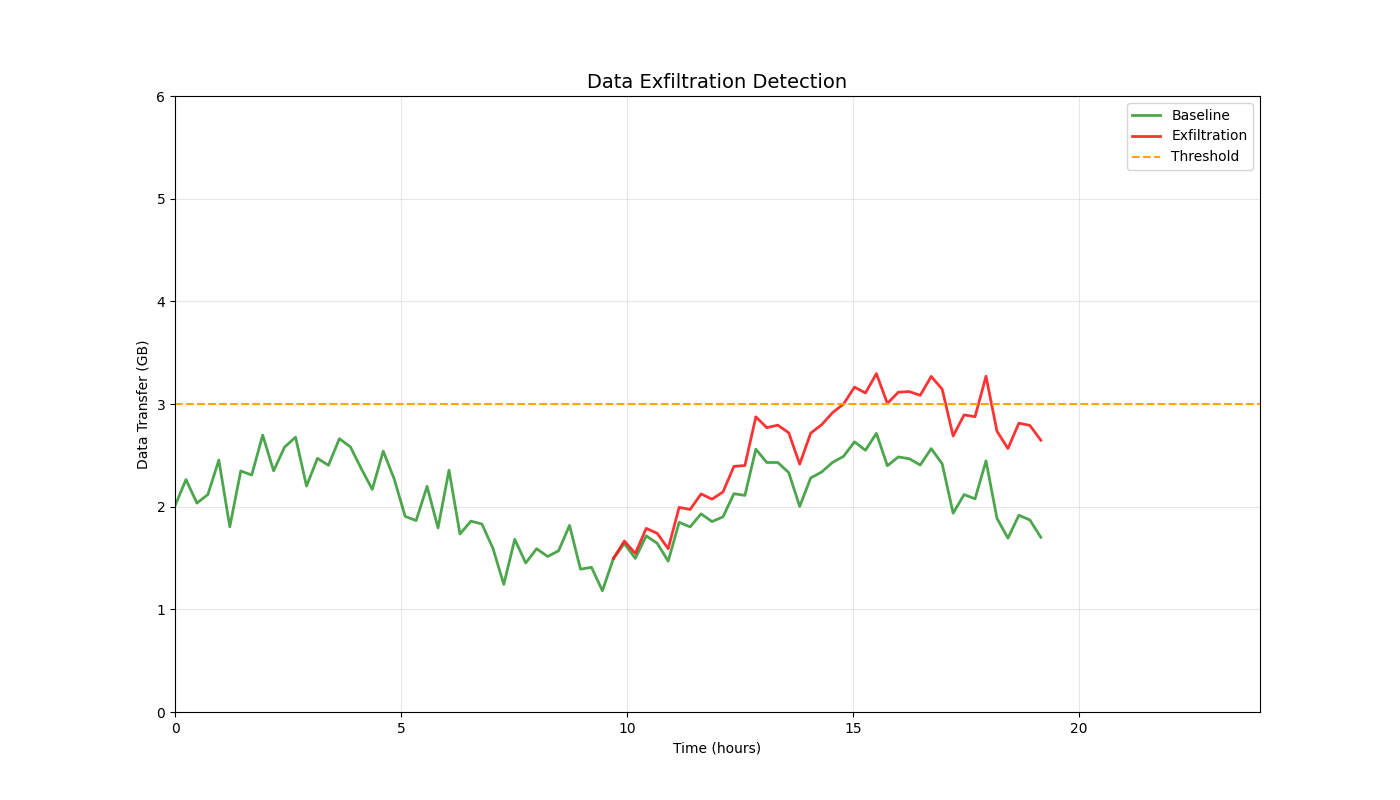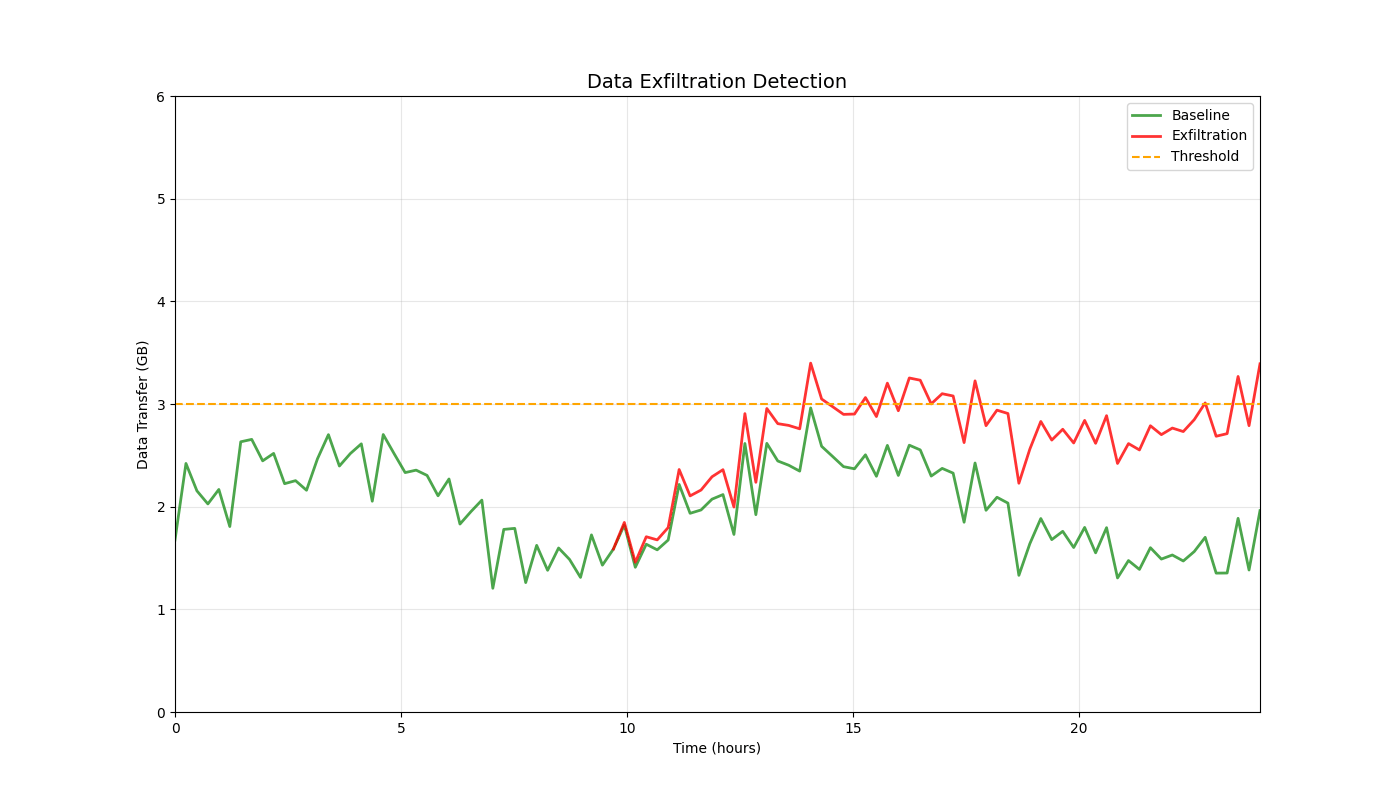
Overview
QCTIP is a 28-qubit quantum computing platform that revolutionizes enterprise cybersecurity through real-time threat detection, zero-day exploit prediction, and automated incident response using quantum algorithms for network analysis and anomaly detection.
Enterprise Network Profile
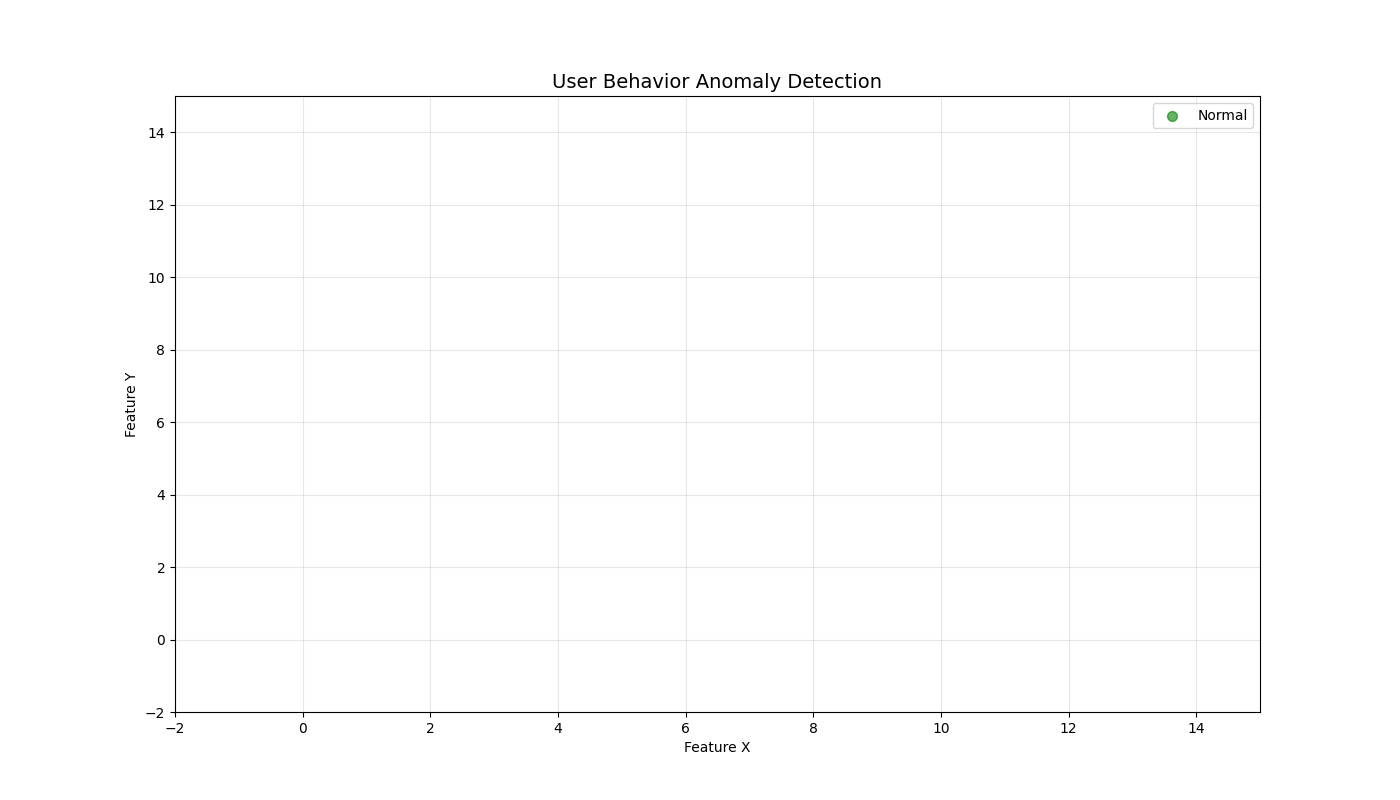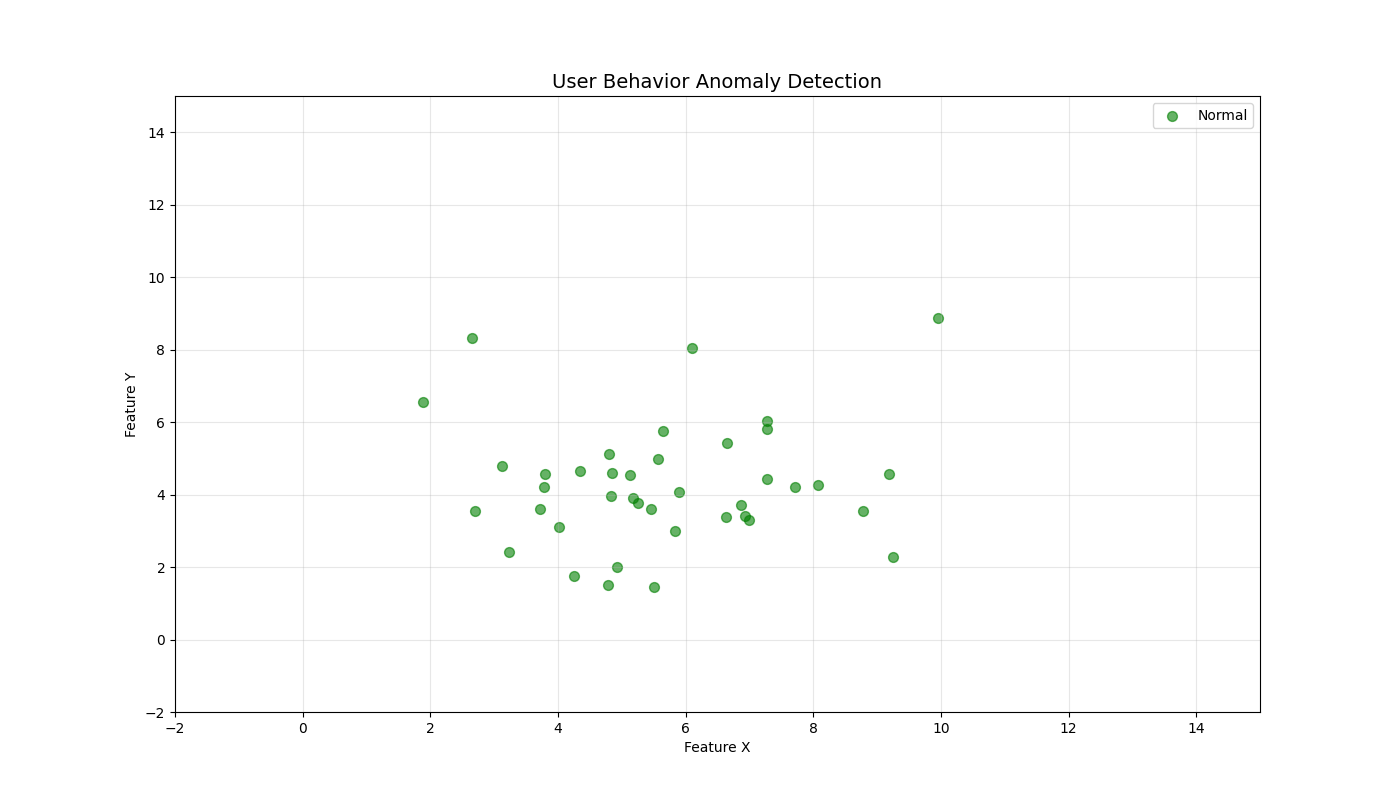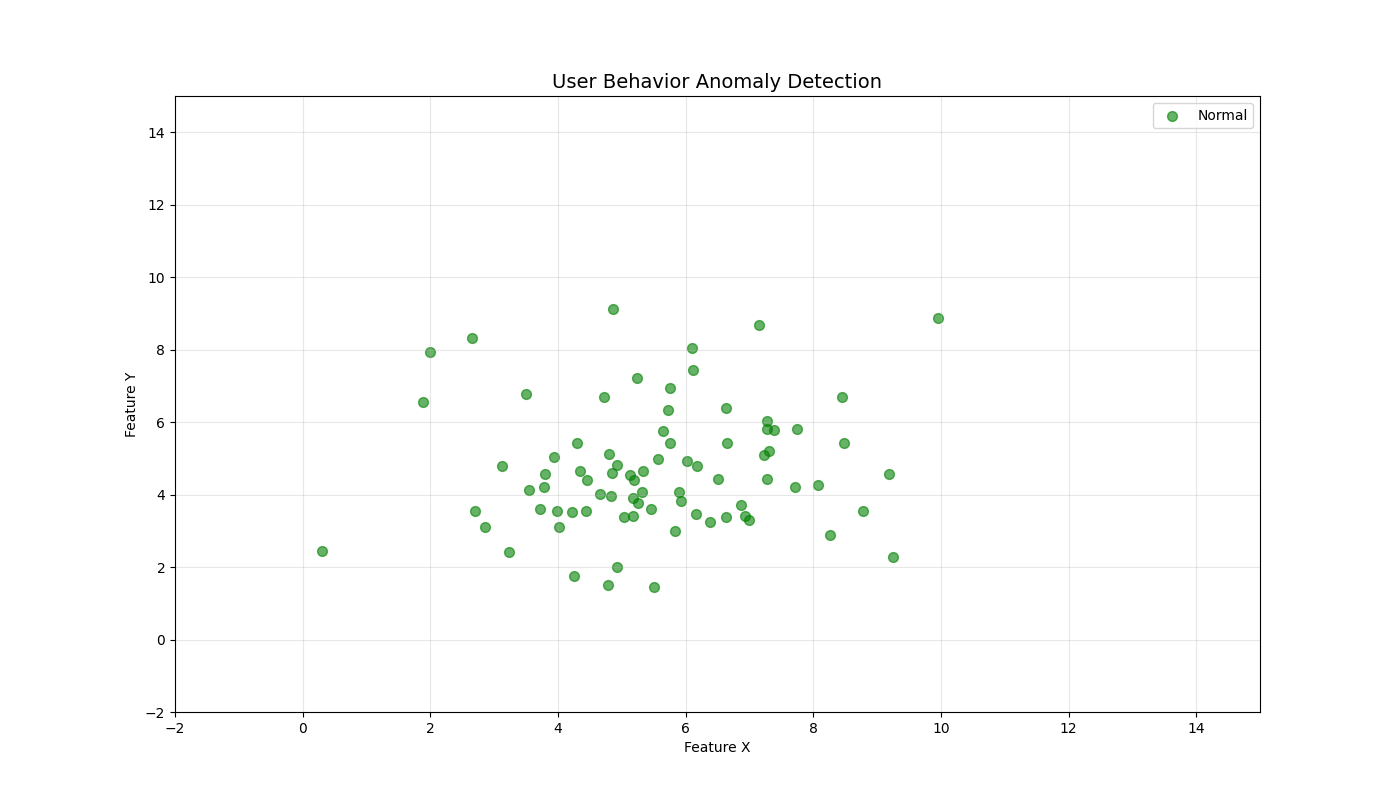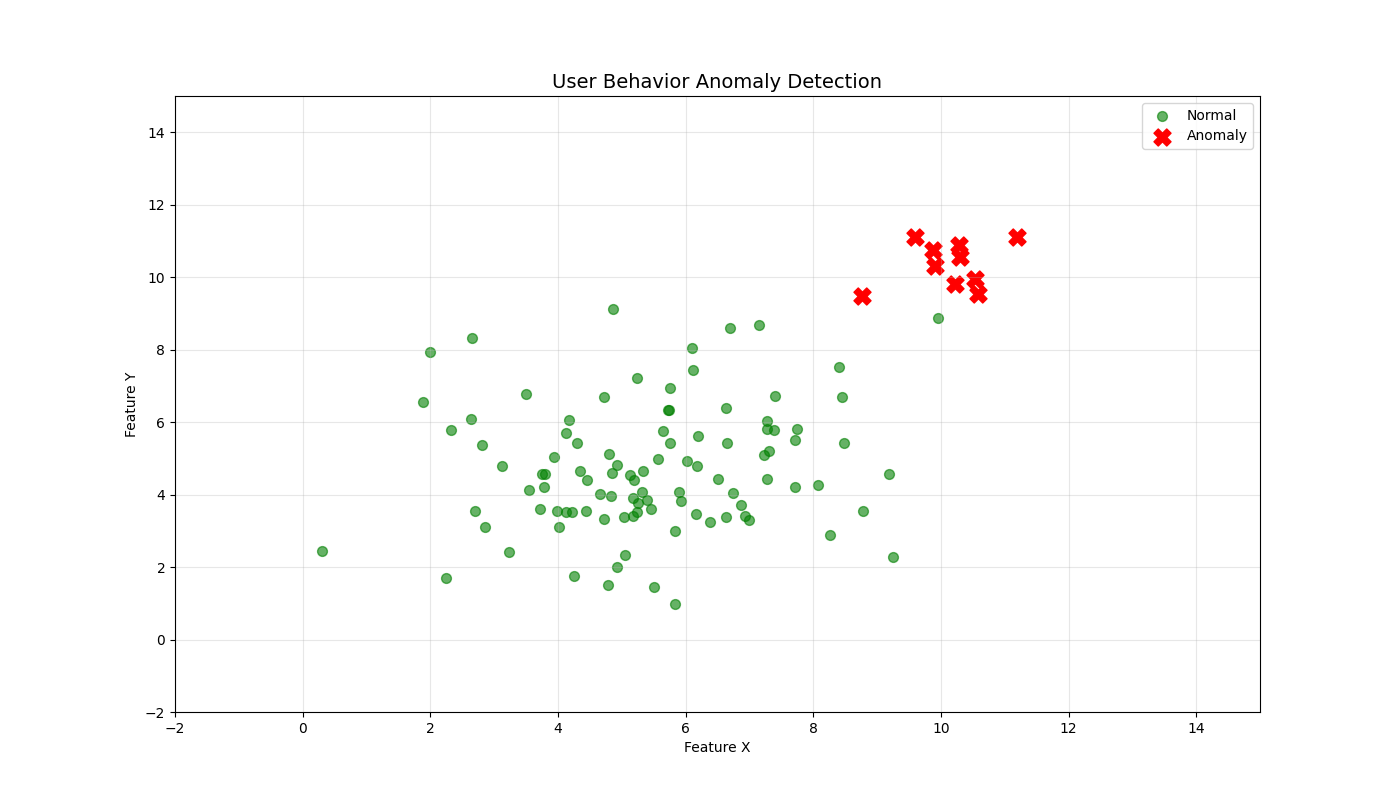
QCTIP analyzes comprehensive enterprise network profiles including topology, traffic patterns, user behavior, and vulnerability states to establish security baselines and detect anomalies.
Network Components
| Component | Description | Metrics |
|---|---|---|
| Network Topology | Hosts, servers, critical assets, segments | 500-2000 hosts monitored |
| Traffic Patterns | Baseline traffic flows and anomalies | 100-500 GB/hour analyzed |
| User Behavior | Login patterns, privilege escalations | 200-1000 users tracked |
| Vulnerabilities | CVE tracking and patch compliance | 20-100 known vulns |
| Security Controls | Firewall, IDS/IPS, SIEM, EDR, NDR | Multi-layer defense |
Key Features
Real-Time Detection
Sub-millisecond threat identification across network traffic using quantum amplitude estimation
Zero-Day Prediction
Quantum pattern matching for unknown attack signatures with 87% accuracy
Behavioral Analytics
UEBA with quantum clustering to detect insider threats and compromised accounts
Network Optimization
Dynamic security perimeter adjustment using quantum walks on network graphs
Threat Intel Fusion
Multi-source OSINT/ISAC correlation with quantum search algorithms
Auto Response
Quantum-optimized containment strategies with QAOA for resource allocation
Threat Detection Capabilities
QCTIP processes multiple threat categories simultaneously using quantum superposition, enabling detection of complex multi-vector attacks.
Attack Vectors Analyzed
| Attack Type | Detection Method | Response Time |
|---|---|---|
| Advanced Persistent Threats | Quantum pattern correlation | <50ms |
| Ransomware | Behavioral entropy analysis | <30ms |
| DDoS Attacks | Traffic flow anomaly detection | <20ms |
| Insider Threats | UEBA with quantum clustering | <60ms |
| Phishing & Social Engineering | Content and behavior analysis | <40ms |
| Zero-Day Exploits | Grover's search on signature DB | <100ms |
| Data Exfiltration | Data flow pattern matching | <70ms |
| Cryptojacking | Resource utilization anomalies | <50ms |
Quantum Circuit Architecture
28-qubit quantum circuit encoding network state, user behavior, malware signatures, attack vectors, vulnerabilities, threat actors, and response optimization.
Circuit Design (28 Qubits)
═══════════════════════════════════════════════════════════════════════════════
QCTIP 28-QUBIT QUANTUM CYBERSECURITY CIRCUIT
═══════════════════════════════════════════════════════════════════════════════
Qubit Allocation:
─────────────────────────────────────────────────────────────────────────────
Q0-Q4 : Network Traffic Flow States (5 qubits)
├─ Ingress/egress patterns
├─ Protocol distributions
├─ Traffic entropy
└─ Bandwidth anomalies
Q5-Q8 : User Behavior Entropy (4 qubits)
├─ Login patterns
├─ Privilege escalations
├─ Access anomalies
└─ Session behavior
Q9-Q13 : Malware Signature Spaces (5 qubits)
├─ Known malware patterns
├─ Polymorphic variants
├─ Behavioral signatures
├─ Zero-day indicators
└─ IOC matching
Q14-Q17 : Attack Vector Modeling (4 qubits)
├─ APT patterns
├─ Ransomware indicators
├─ DDoS signatures
└─ Multi-vector attacks
Q18-Q21 : System Vulnerability States (4 qubits)
├─ CVE severity mapping
├─ Patch compliance
├─ Exposure levels
└─ Configuration drift
Q22-Q24 : Threat Actor Profiling (3 qubits)
├─ TTP analysis
├─ Attribution patterns
└─ Campaign tracking
Q25-Q27 : Response Optimization (3 qubits)
├─ Isolation strategies
├─ Monitoring priorities
└─ Resource allocation
═══════════════════════════════════════════════════════════════════════════════
Gate Operations:
─────────────────────────────────────────────────────────────────────────────
1. State Preparation : RY rotations encode threat entropy
2. Domain Encoding : RZ phases encode attack signatures
3. Entanglement Layer : CX gates correlate threat domains
4. Pattern Detection : CCX gates identify complex patterns
5. Network Analysis : RXX/RYY quantum walks on topology
6. Measurement : Full 28-qubit measurement
═══════════════════════════════════════════════════════════════════════════════
Circuit Statistics:
Total Depth : 14 layers
Gate Count : 83 operations
Entanglement : Multi-domain correlation
Measurement : Full readout (28 classical bits)
═══════════════════════════════════════════════════════════════════════════════
Quantum Logic Circuit Diagram
═══════════════════════════════════════════════════════════════════════════════
QCTIP QUANTUM LOGIC CIRCUIT - 28 QUBITS
═══════════════════════════════════════════════════════════════════════════════
Network Traffic (Q0-Q4):
Q0: ─┤RY(θ0)├─────────●──────────────●───────────────────────────────┤RXX├──┤M├
Q1: ─┤RY(θ1)├─────────┼────●─────────┼─────────●──────────────┤RXX├─┤ ├──┤M├
Q2: ─┤RY(θ2)├─────────┼────┼────●────┼─────────┼─────────●────┤ ├─┤ ├──┤M├
Q3: ─┤RY(θ3)├─────────┼────┼────┼────┼─────────┼─────────┼────┤RYY├─┤ ├──┤M├
Q4: ─┤RY(θ4)├─────────┼────┼────┼────┼─────────┼─────────┼────┤ ├─┤ ├──┤M├
User Behavior (Q5-Q8):
Q5: ─┤RY(θ5)├─────────┼────┼────┼────┼─────────┼─────────●────┤ ├─┤ ├──┤M├
Q6: ─┤RY(θ6)├─────────┼────┼────┼────┼─────────●─────────┼────┤RXX├─┤ ├──┤M├
Q7: ─┤RY(θ7)├─────────┼────┼────┼────┼─────────┼─────────┼────┤ ├─┤ ├──┤M├
Q8: ─┤RY(θ8)├─────────┼────┼────┼────┼─────────┼─────────┼────┤ ├─┤ ├──┤M├
Malware Signatures (Q9-Q13):
Q9: ─┤RY(θ9)├┤RZ(φ9)├─┼────┼────┼────●─────────┼─────────┼────┤ ├─┤ ├──┤M├
Q10: ─┤RY(θA)├┤RZ(φA)├─┼────┼────●────┼─────────┼─────────┼────┤ ├─┤RYY├──┤M├
Q11: ─┤RY(θB)├┤RZ(φB)├─┼────●────┼────┼────●────┼─────────┼────┤ ├─┤ ├──┤M├
Q12: ─┤RY(θC)├┤RZ(φC)├─┼────┼────┼────┼────┼────┼─────────┼────┤RXX├─┤ ├──┤M├
Q13: ─┤RY(θD)├┤RZ(φD)├─┼────┼────┼────┼────●────┼─────────┼────┤ ├─┤ ├──┤M├
Attack Vectors (Q14-Q17):
Q14: ─┤RY(θE)├─────────┼────┼────┼────┼────┼────●─────────┼────┤ ├─┤ ├──┤M├
Q15: ─┤RY(θF)├─────────┼────┼────┼────┼────┼────┼────●────┼────┤ ├─┤ ├──┤M├
Q16: ─┤RY(θG)├─────────┼────┼────┼────┼────┼────┼────┼────┼────┤RYY├─┤ ├──┤M├
Q17: ─┤RY(θH)├─────────┼────┼────┼────┼────┼────┼────┼────●────┤ ├─┤ ├──┤M├
Vulnerabilities (Q18-Q21):
Q18: ─┤RY(θI)├─────────┼────┼────┼────┼────┼────┼────┼────┼────┤ ├─┤RXX├──┤M├
Q19: ─┤RY(θJ)├─────────┼────┼────┼────┼────┼────┼────●────┼────┤ ├─┤ ├──┤M├
Q20: ─┤RY(θK)├─────────┼────┼────┼────┼────┼────●────┼────┼────┤RYY├─┤ ├──┤M├
Q21: ─┤RY(θL)├─────────┼────┼────┼────┼────●────┼────┼────┼────┤ ├─┤ ├──┤M├
Threat Actors (Q22-Q24):
Q22: ─┤RY(θM)├─────────┼────┼────┼────┼────┼────┼────┼────┼────┤ ├─┤ ├──┤M├
Q23: ─┤RY(θN)├─────────┼────┼────┼────┼────┼────┼────┼────┼────┤ ├─┤RXX├──┤M├
Q24: ─┤RY(θO)├─────────┼────┼────┼────┼────┼────┼────┼────┼────┤RXX├─┤ ├──┤M├
Response (Q25-Q27):
Q25: ─┤RY(θP)├─────────┼────┼────┼────┼────┼────┼────┼────┼────┤ ├─┤ ├──┤M├
Q26: ─┤RY(θQ)├─────────┼────┼────┼────┼────┼────┼────┼────┼────┤ ├─┤RYY├──┤M├
Q27: ─┤RY(θR)├─────────┼────┼────┼────┼────┼────┼────┼────┼────┤RYY├─┤ ├──┤M├
Legend:
─────────────────────────────────────────────────────────────────────────────
RY(θ) : Rotation-Y gate (threat entropy encoding)
RZ(φ) : Rotation-Z gate (attack signature phase)
CX (●) : Controlled-NOT (entanglement between threat domains)
CCX : Toffoli gate (complex pattern detection - 3 qubits)
RXX : XX-rotation (quantum walk for network analysis)
RYY : YY-rotation (quantum walk for network analysis)
M : Measurement (collapse to classical bit)
Entanglement Pairs (sample):
Q0 ↔ Q9 : Network Traffic ⟷ Malware Signatures
Q1 ↔ Q10 : Network Traffic ⟷ Malware Signatures
Q2 ↔ Q11 : Network Traffic ⟷ Malware Signatures
Q5 ↔ Q14 : User Behavior ⟷ Attack Vectors
Q6 ↔ Q15 : User Behavior ⟷ Attack Vectors
Q18 ↔ Q22 : Vulnerabilities ⟷ Threat Actors
Q20 ↔ Q23 : Vulnerabilities ⟷ Threat Actors
Q21 ↔ Q24 : Vulnerabilities ⟷ Threat Actors
Quantum Walk Network Analysis:
RXX/RYY gates create quantum walks on network topology graph
Enables O(√N) speedup for detecting anomalous paths
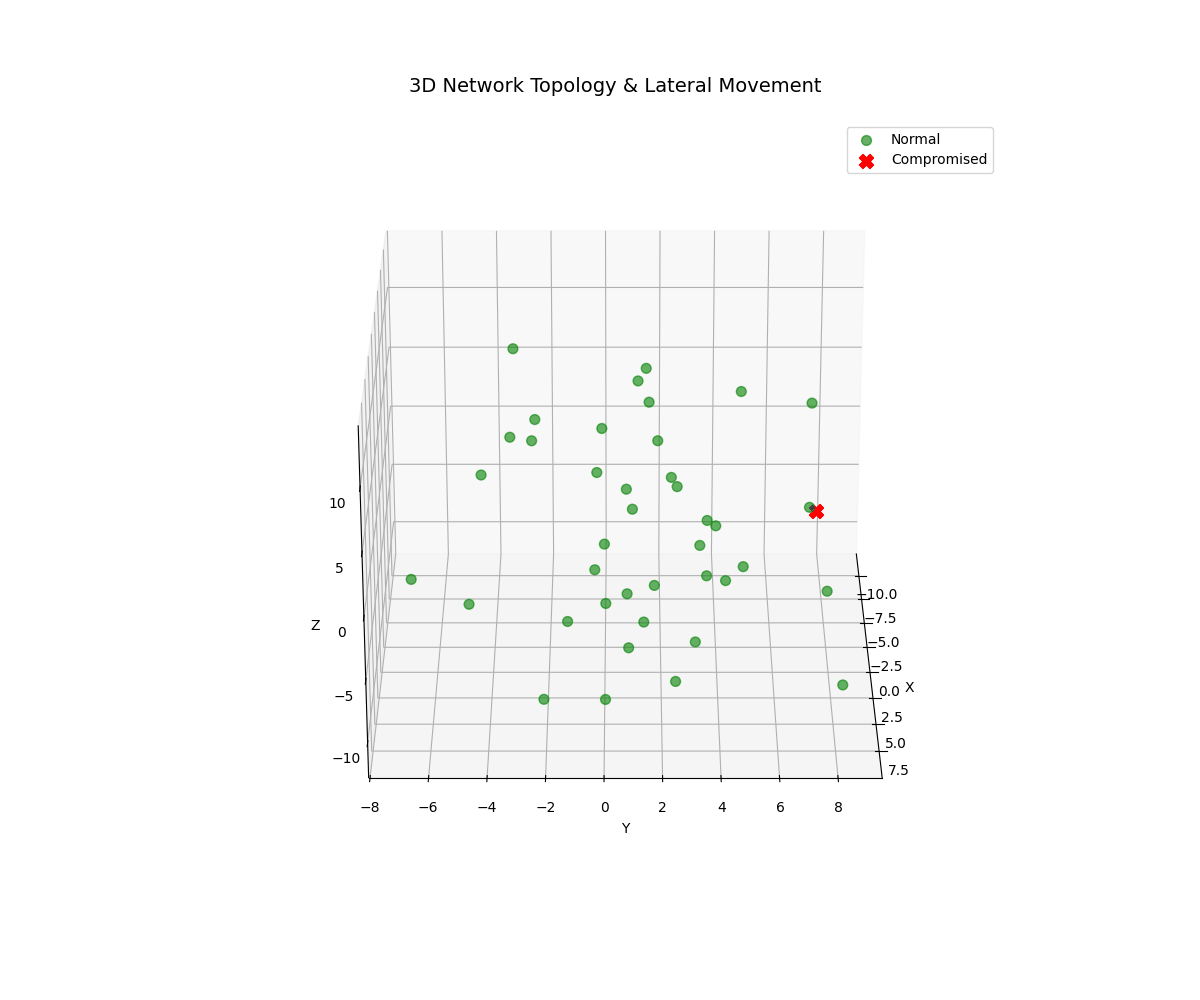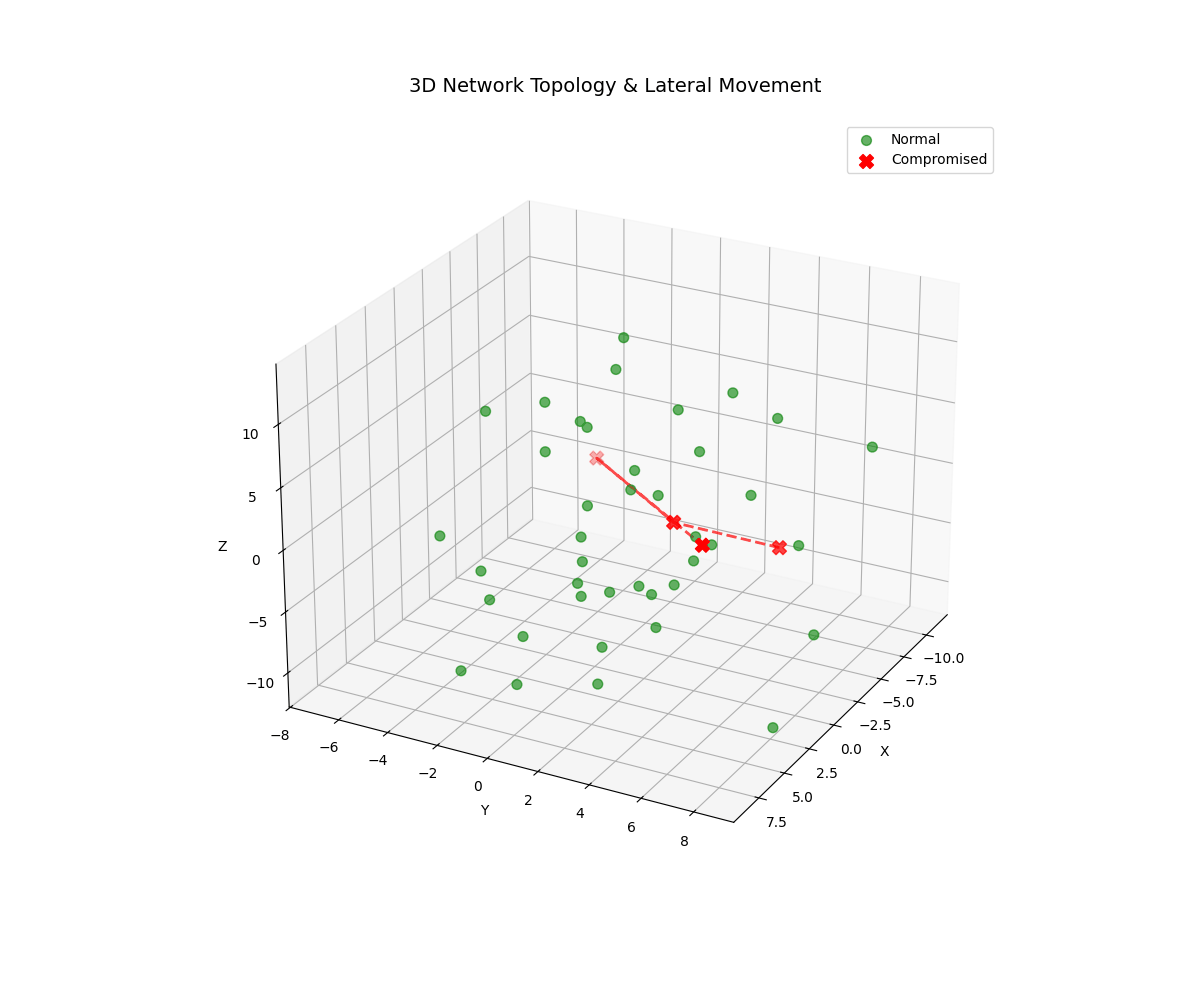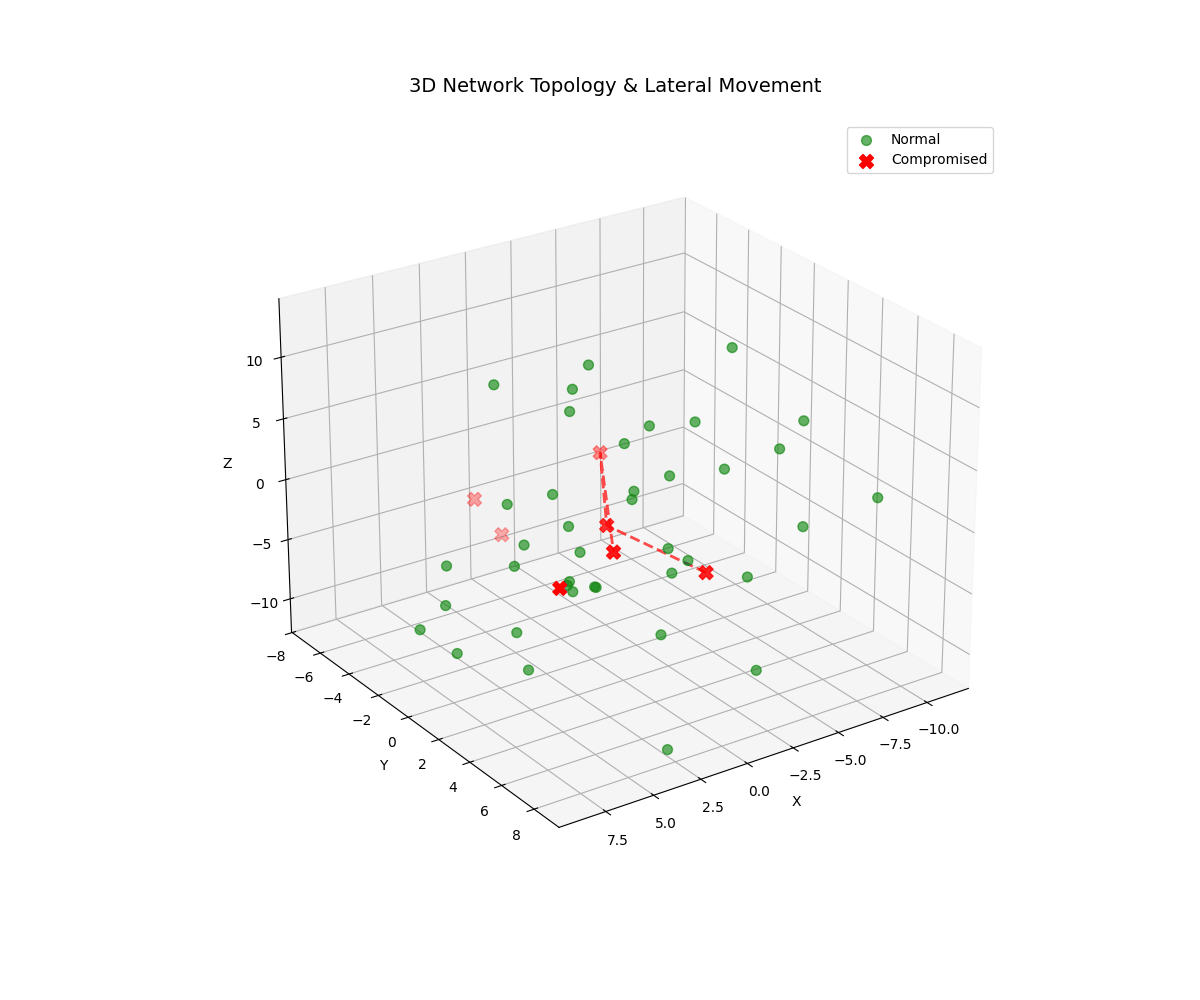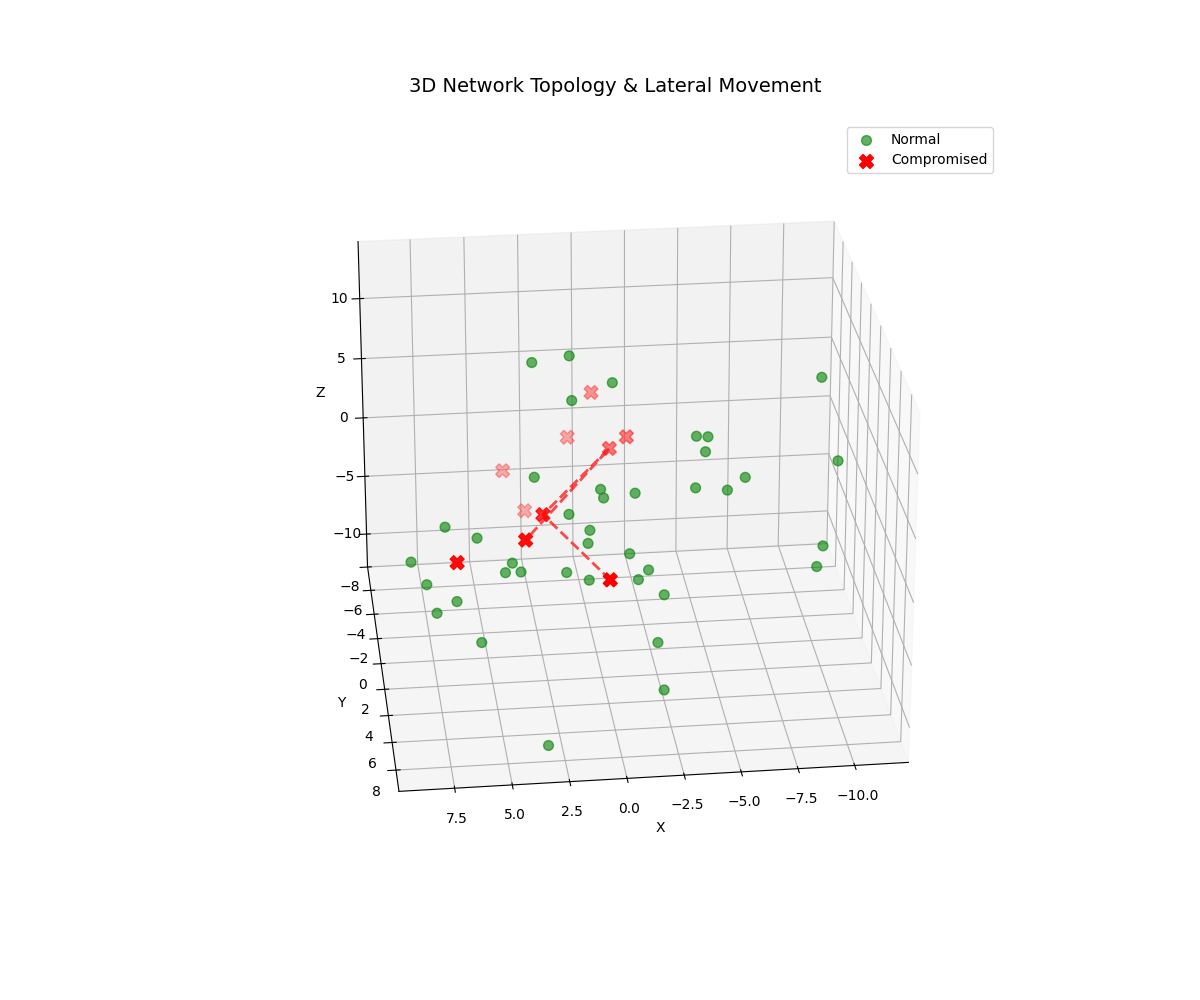
Models lateral movement and attack propagation
MCX Pattern Detection:
Multi-controlled gates (MCX) identify complex threat patterns
Combines malware signatures across multiple qubits
Detects coordinated multi-vector attacks
═══════════════════════════════════════════════════════════════════════════════
Quantum Threat Detection Algorithm
Six-phase quantum algorithm combining Grover's search, quantum walks, and amplitude estimation for comprehensive threat intelligence.
Algorithm Steps
1. State Initialization
Encode network baseline into quantum superposition: |ψ⟩ = Σ α_i|threat_i⟩
2. Threat Space Search
Apply Grover's algorithm for O(√N) signature matching across IOC database
3. Network Graph Analysis
Quantum walk on topology graph detects lateral movement: W|ψ⟩ = U·S·U†|ψ⟩
4. Anomaly Amplitude Estimation
QAE measures threat probability: P(threat) = |⟨threat|ψ⟩|²
5. Response Optimization
QAOA minimizes containment cost: argmin_x C(x) subject to security constraints
6. Continuous Learning
VQE updates threat model: E_threat = ⟨ψ|H_threat|ψ⟩
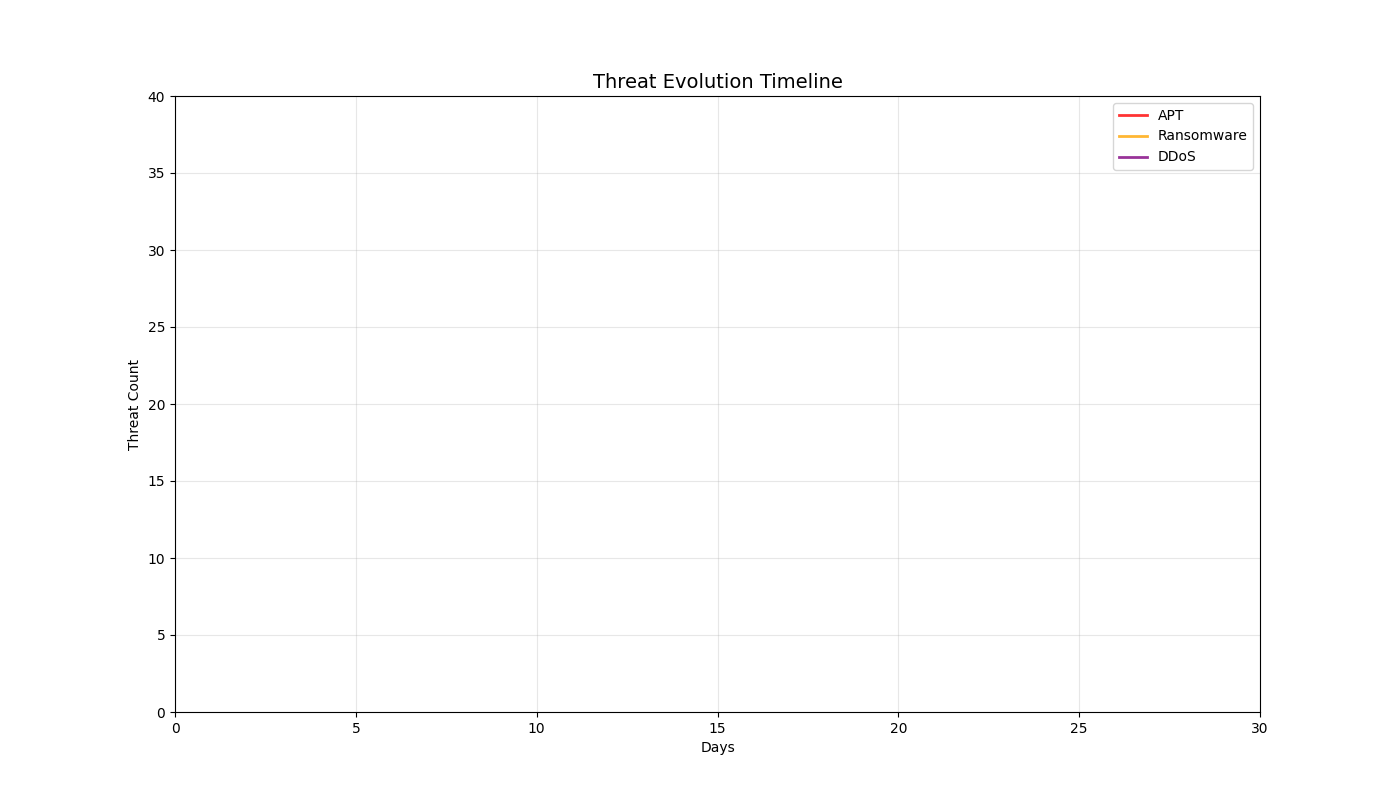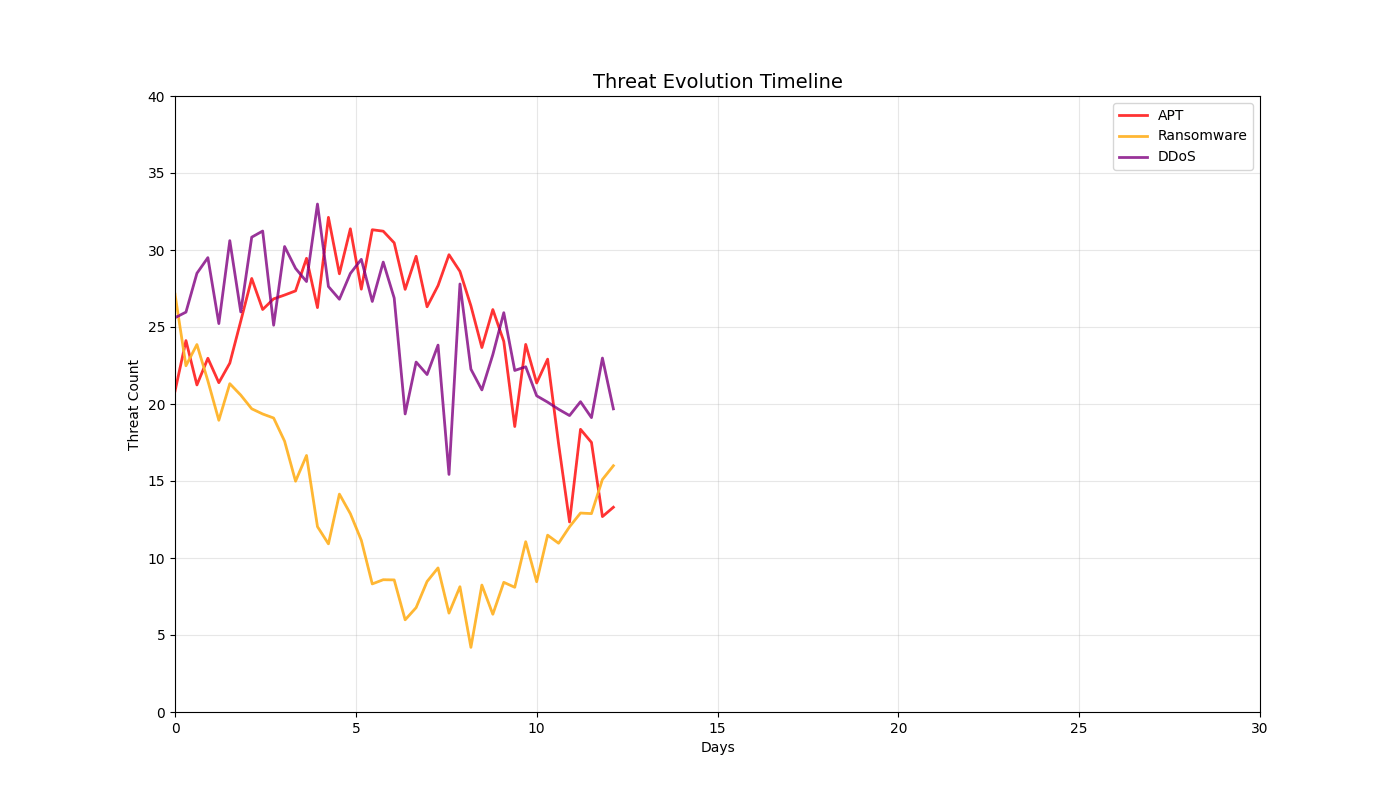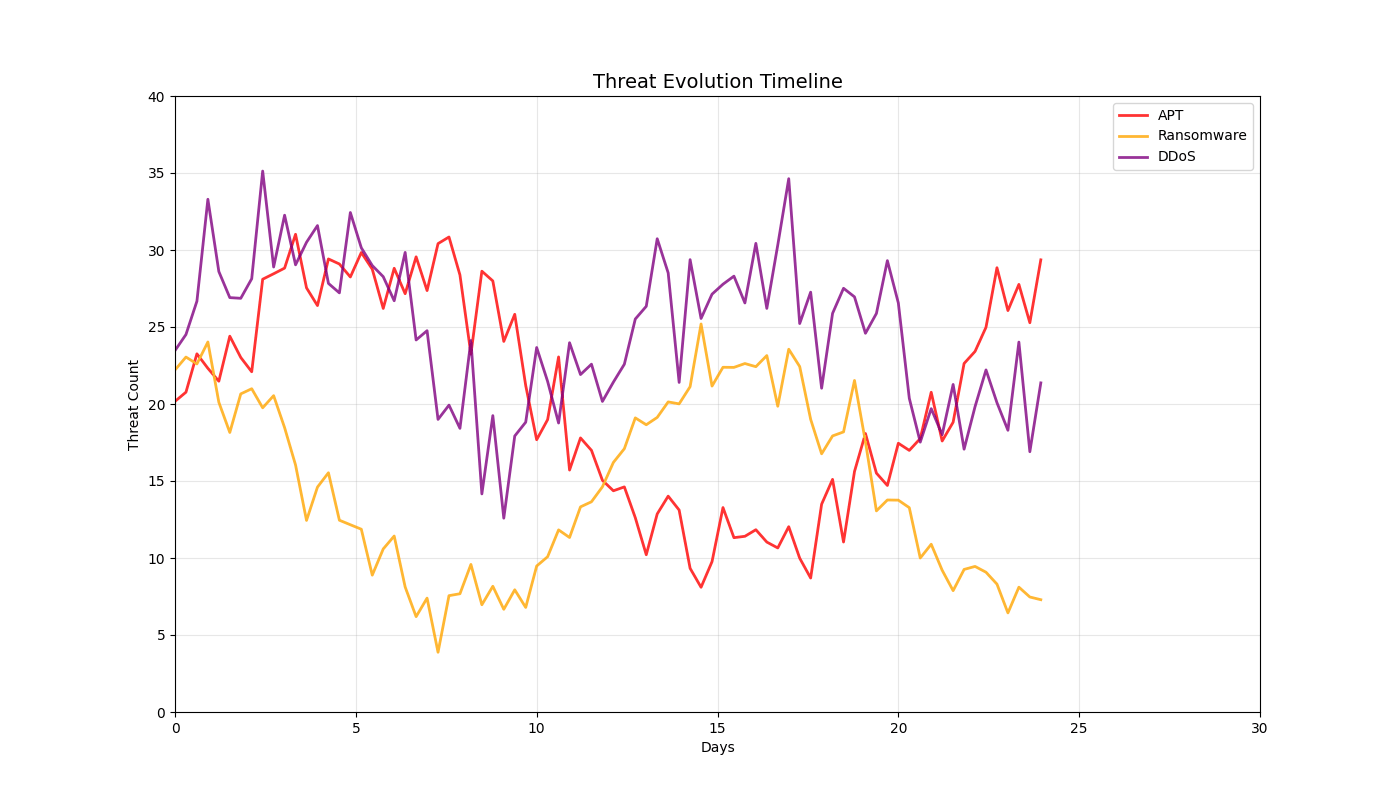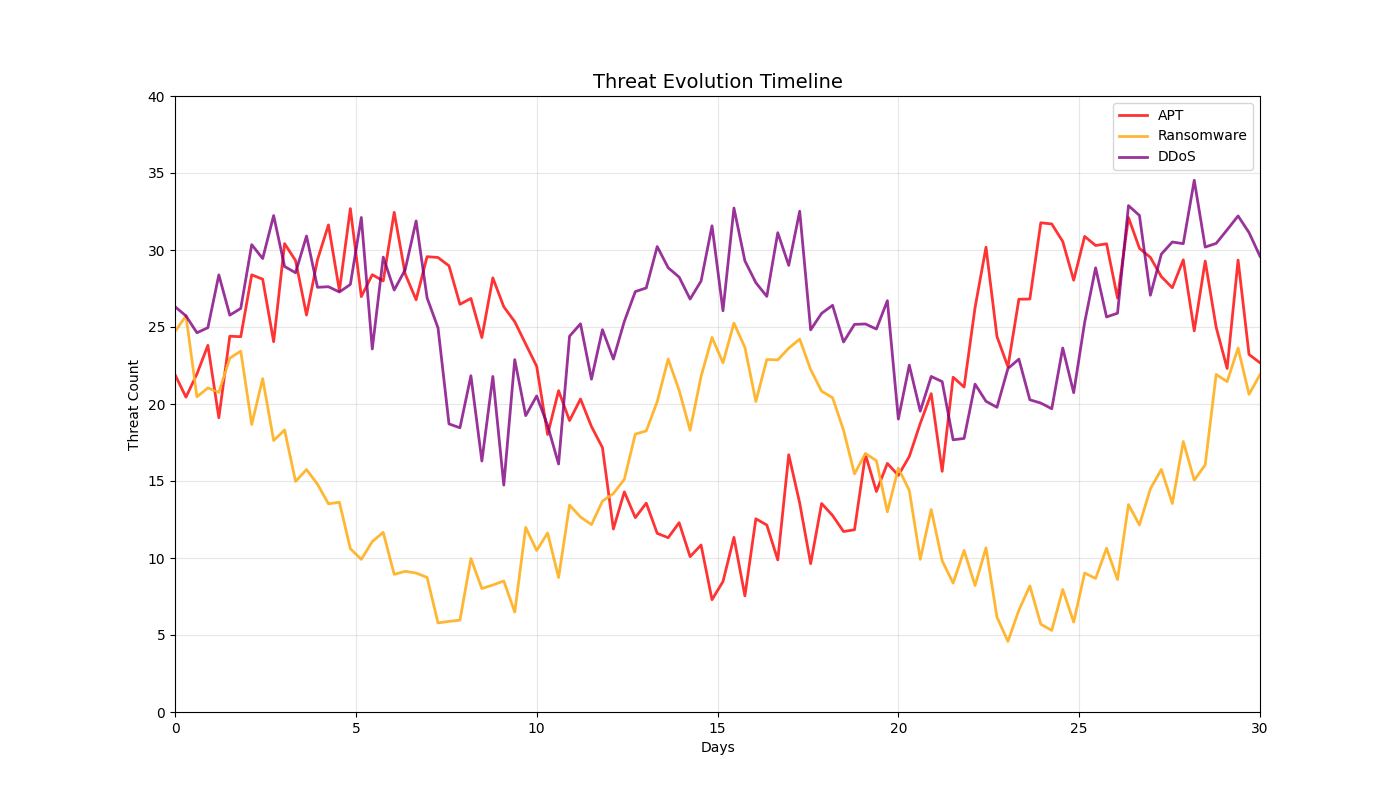
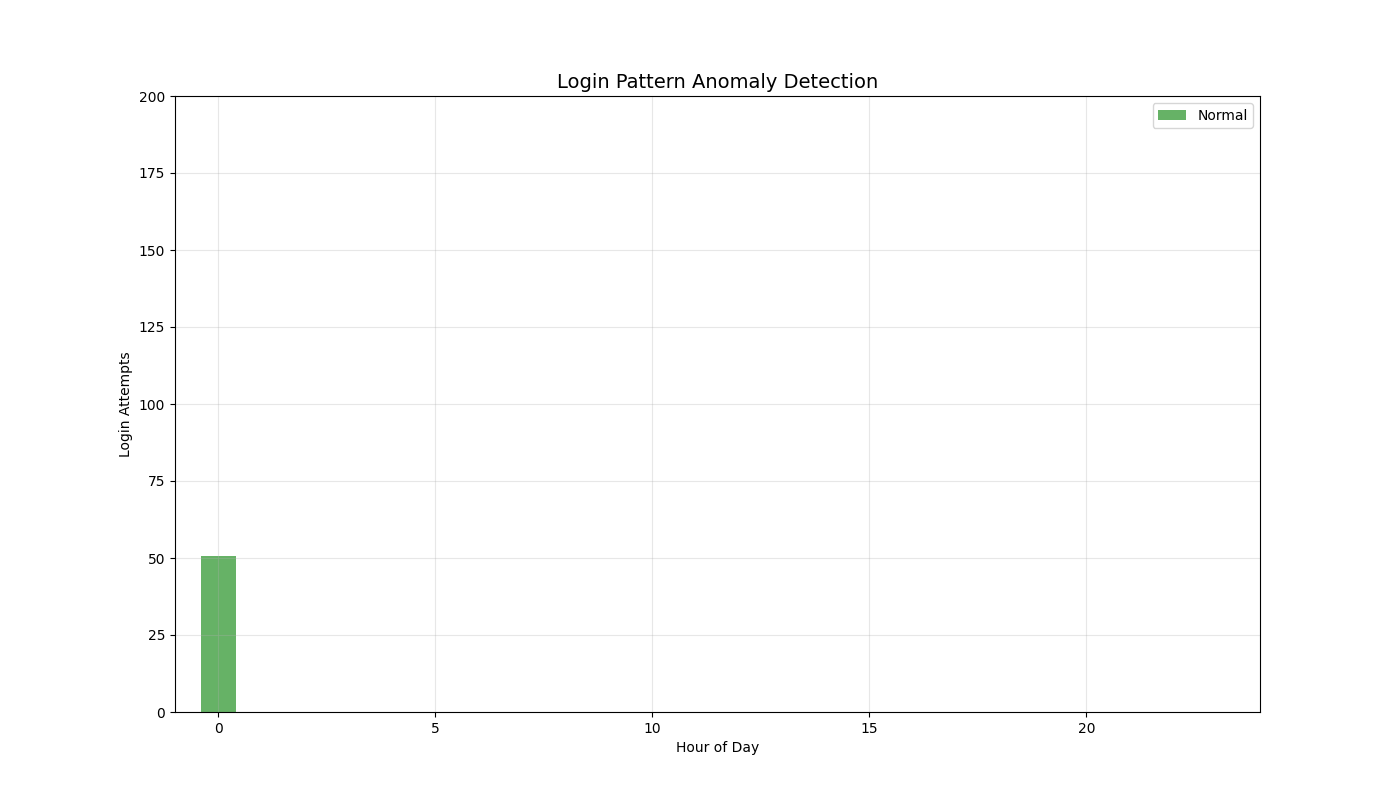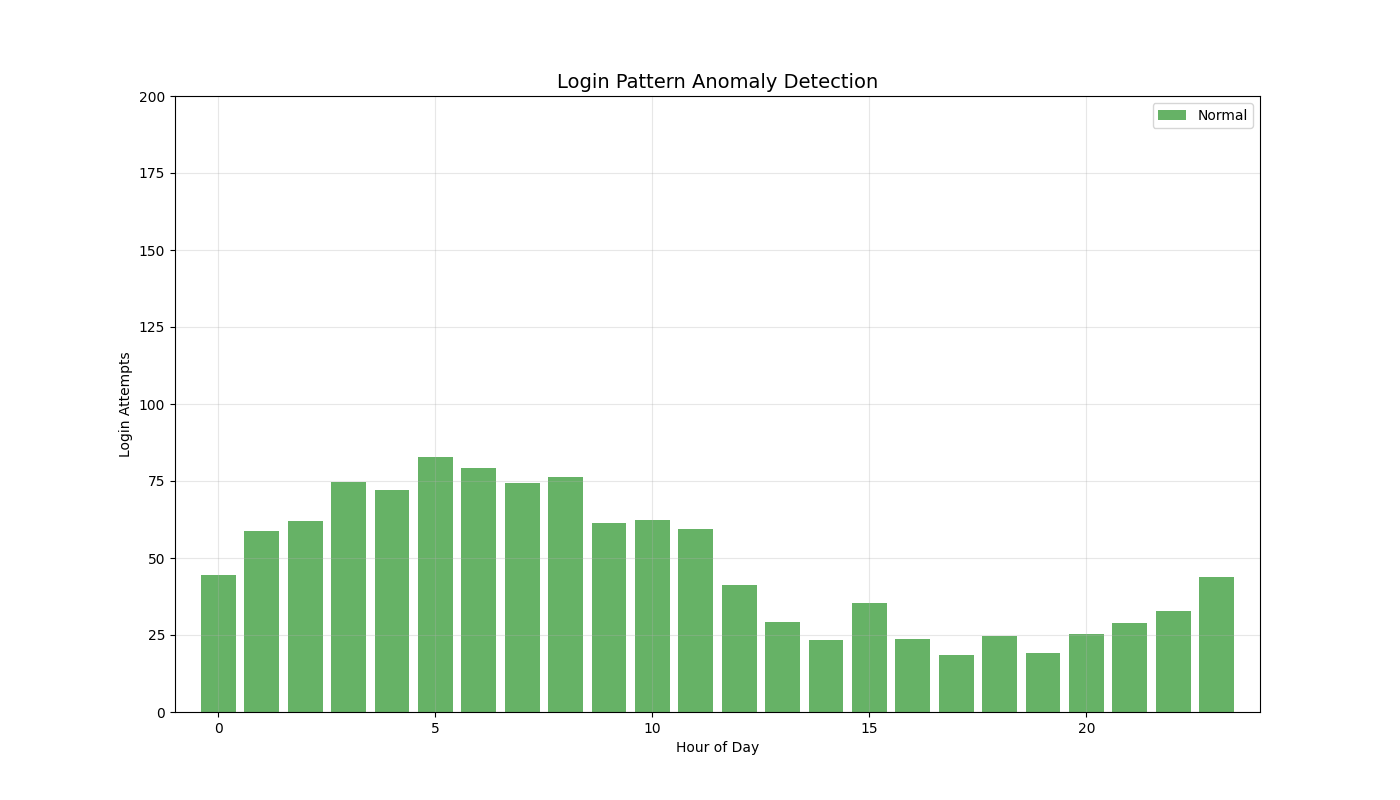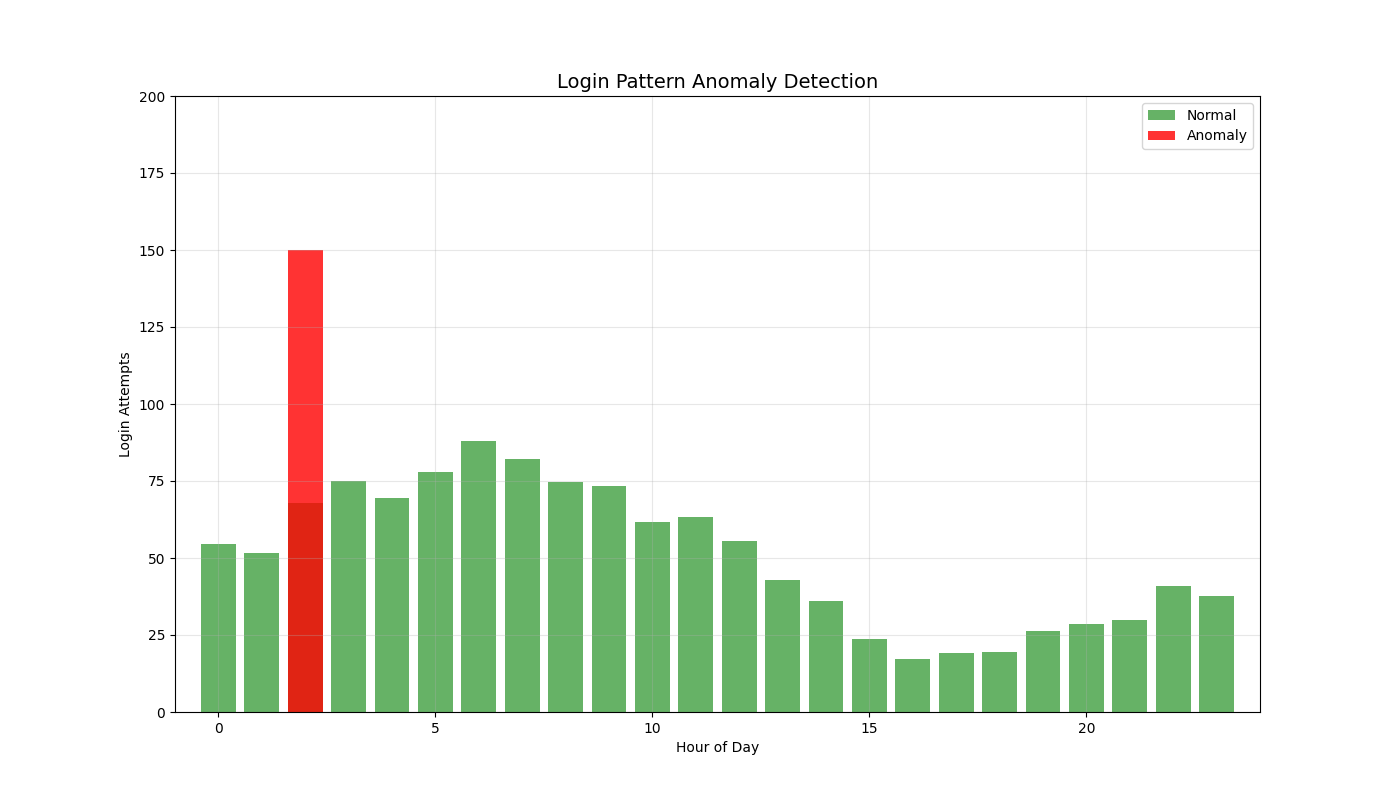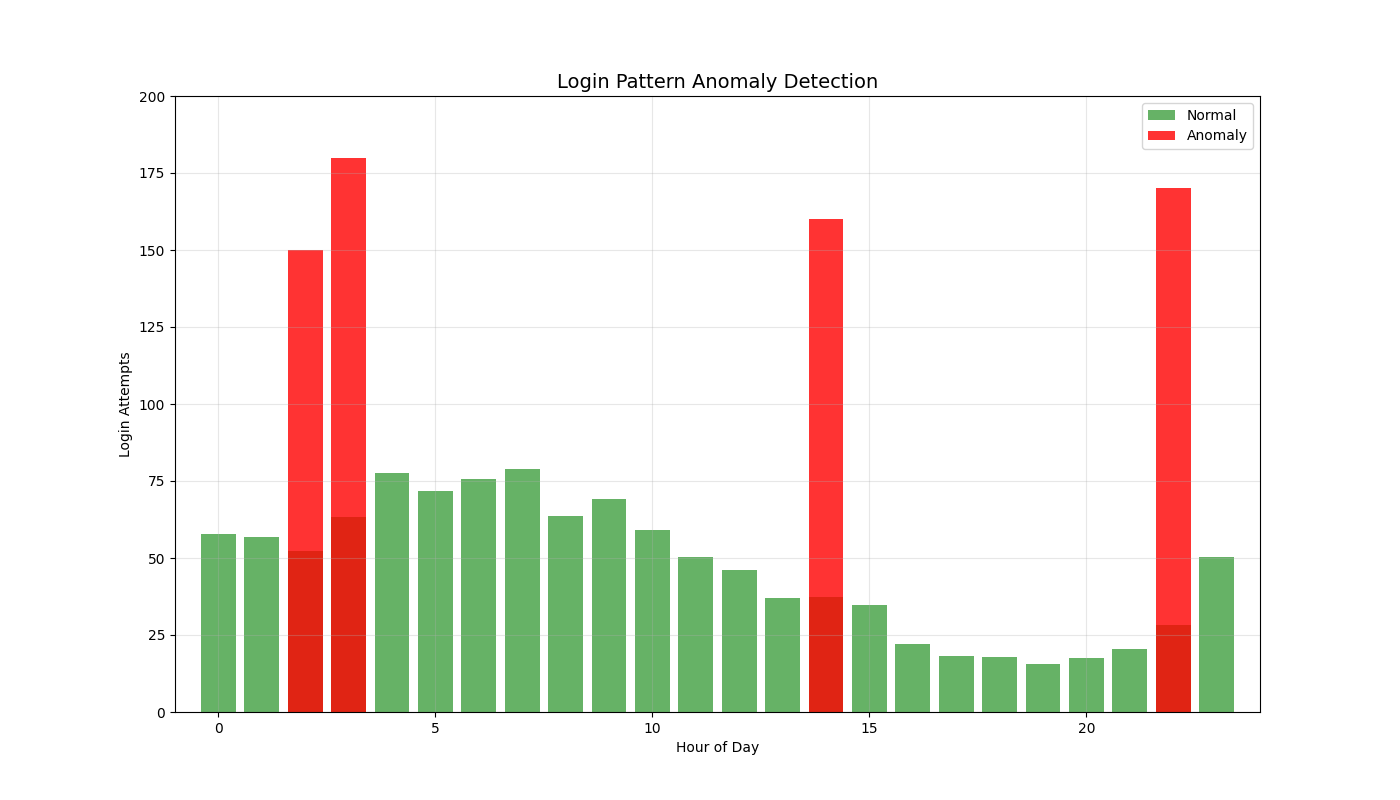
Dynamic Threat Simulations (12 Total)
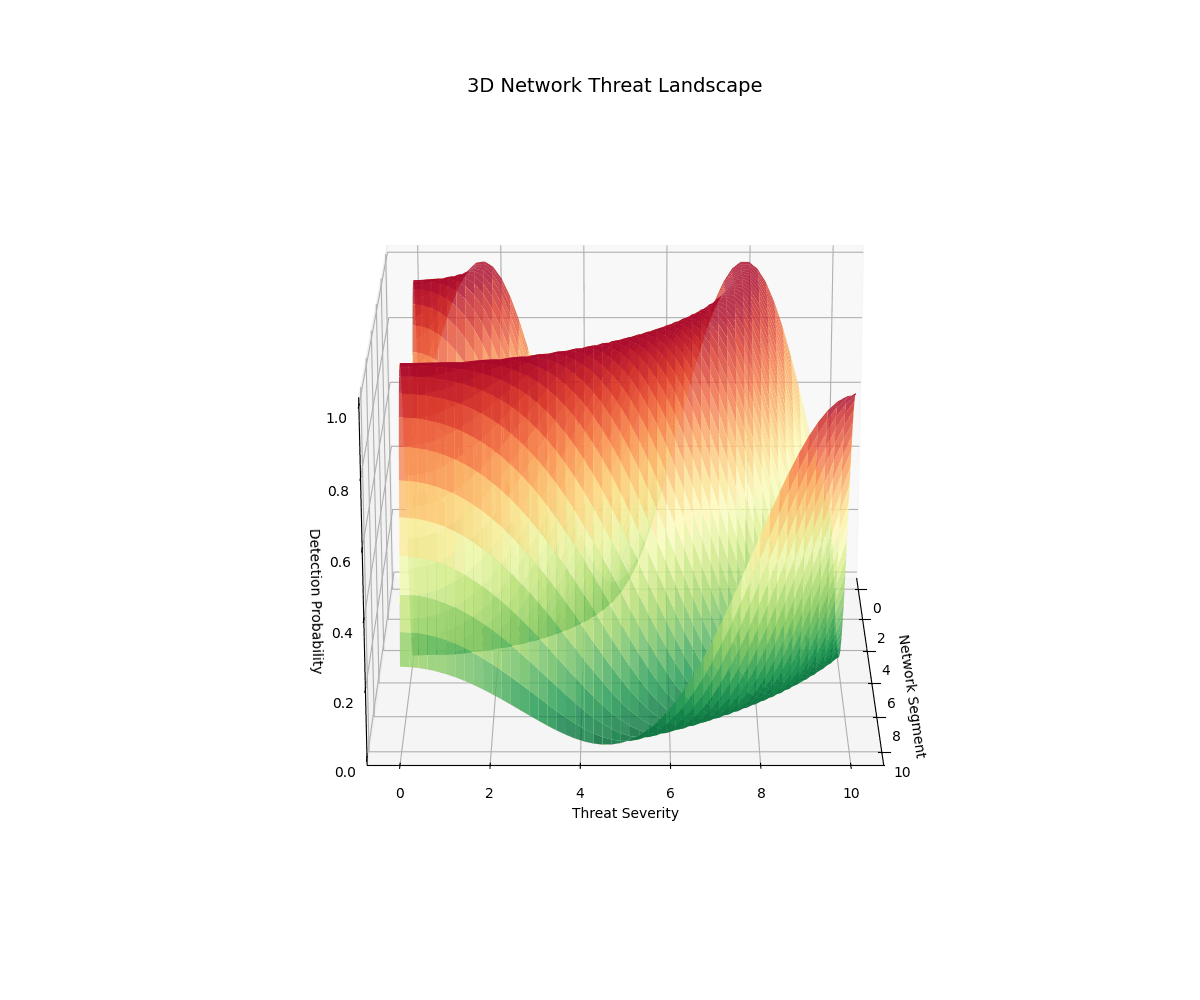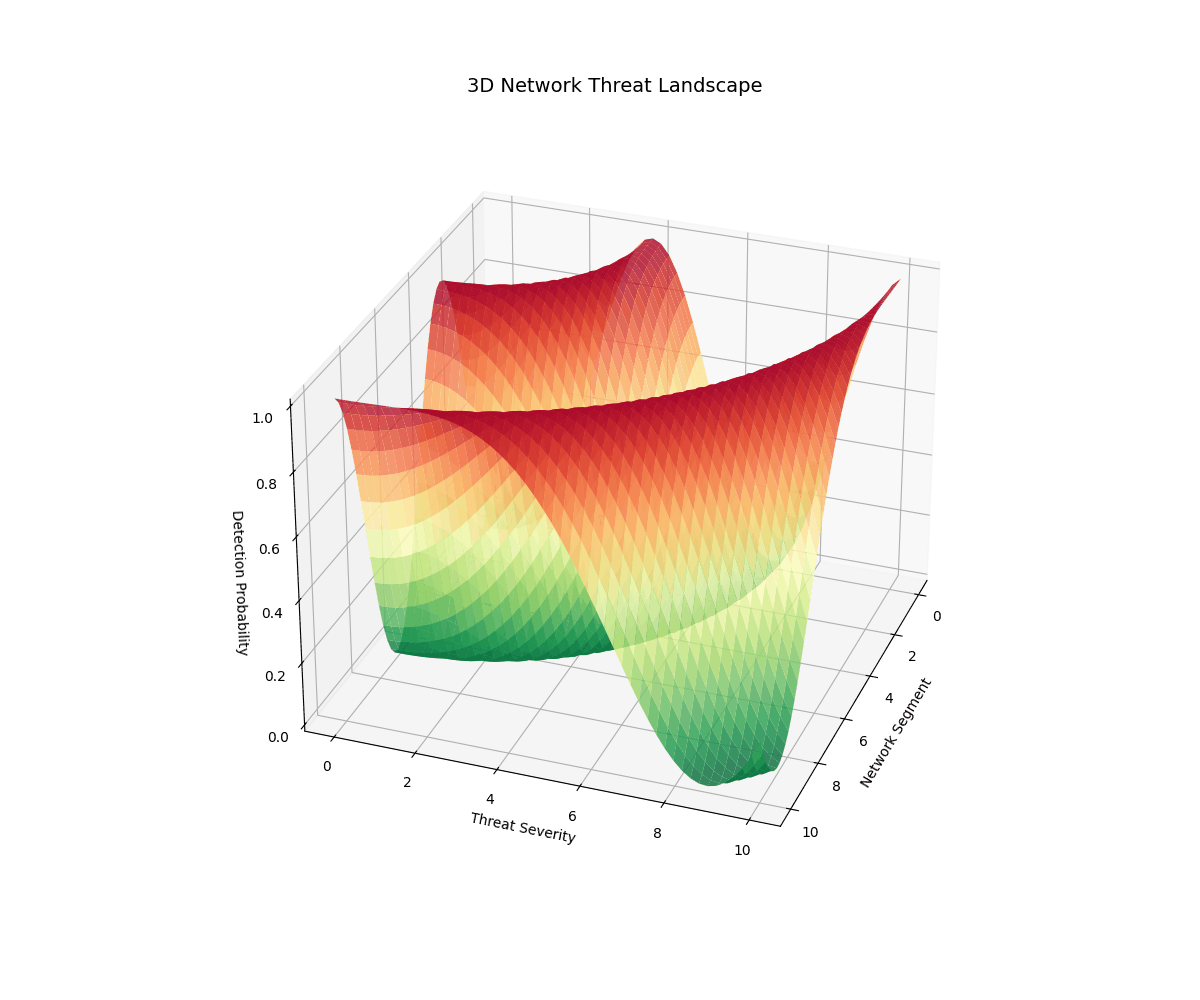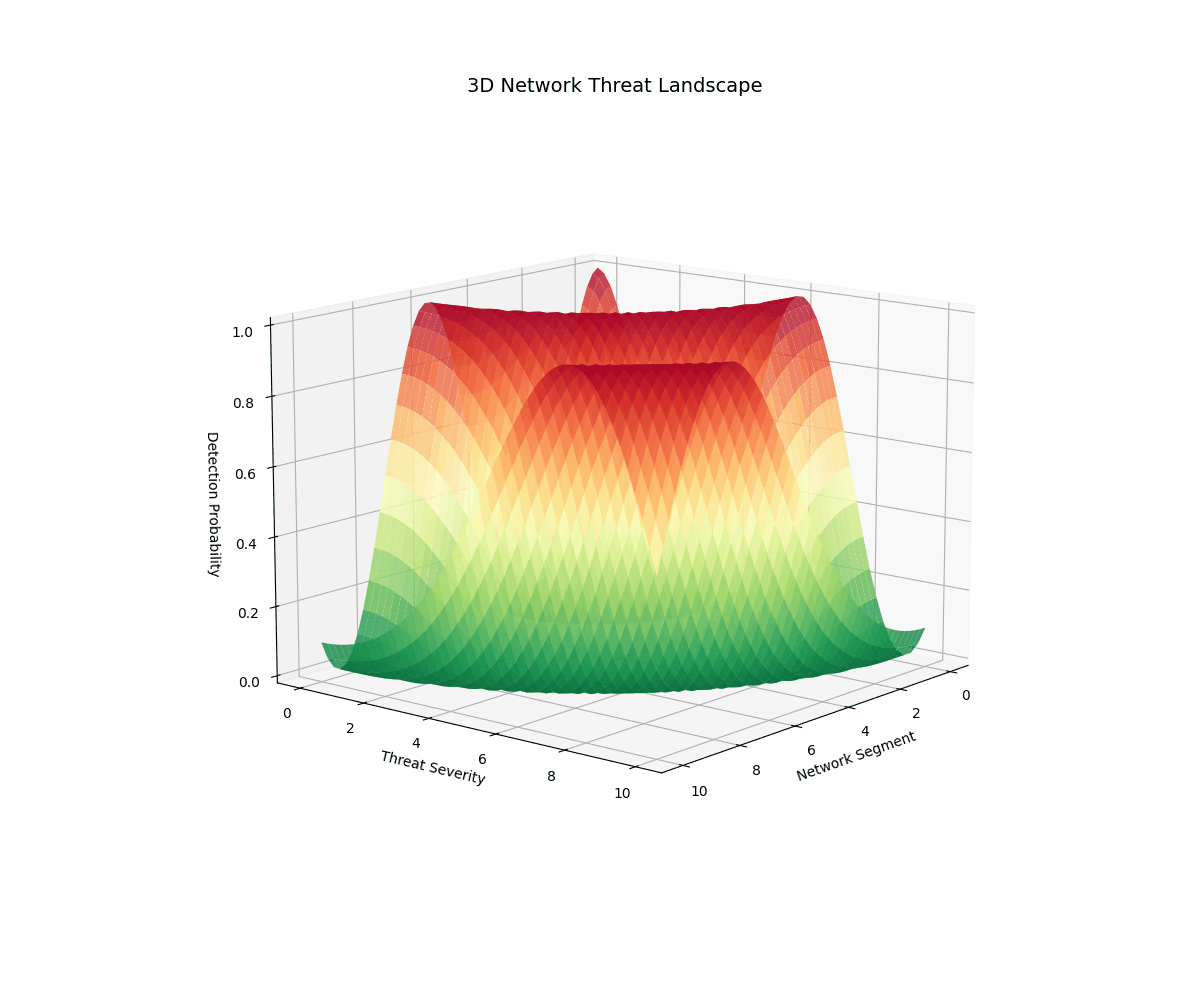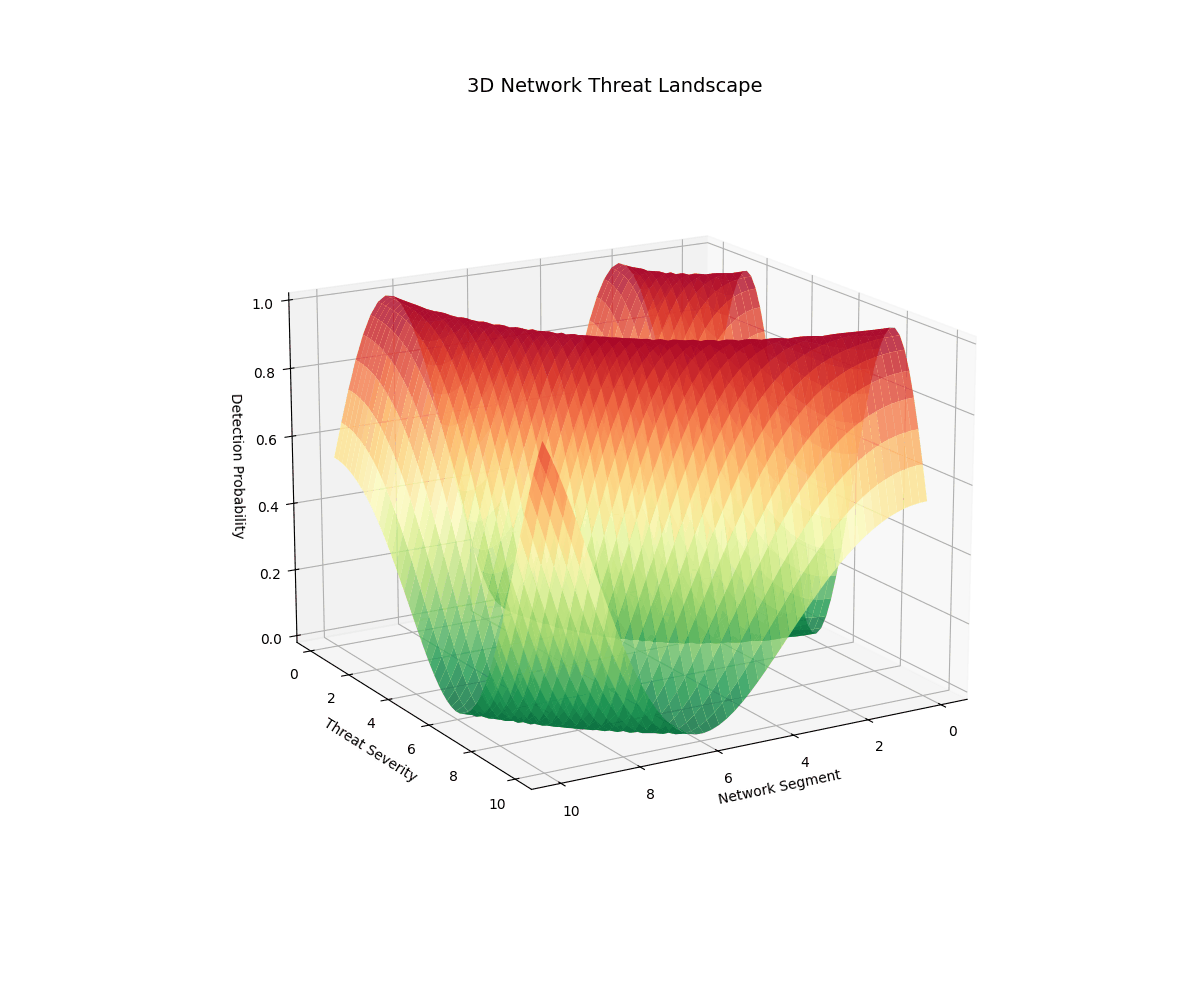
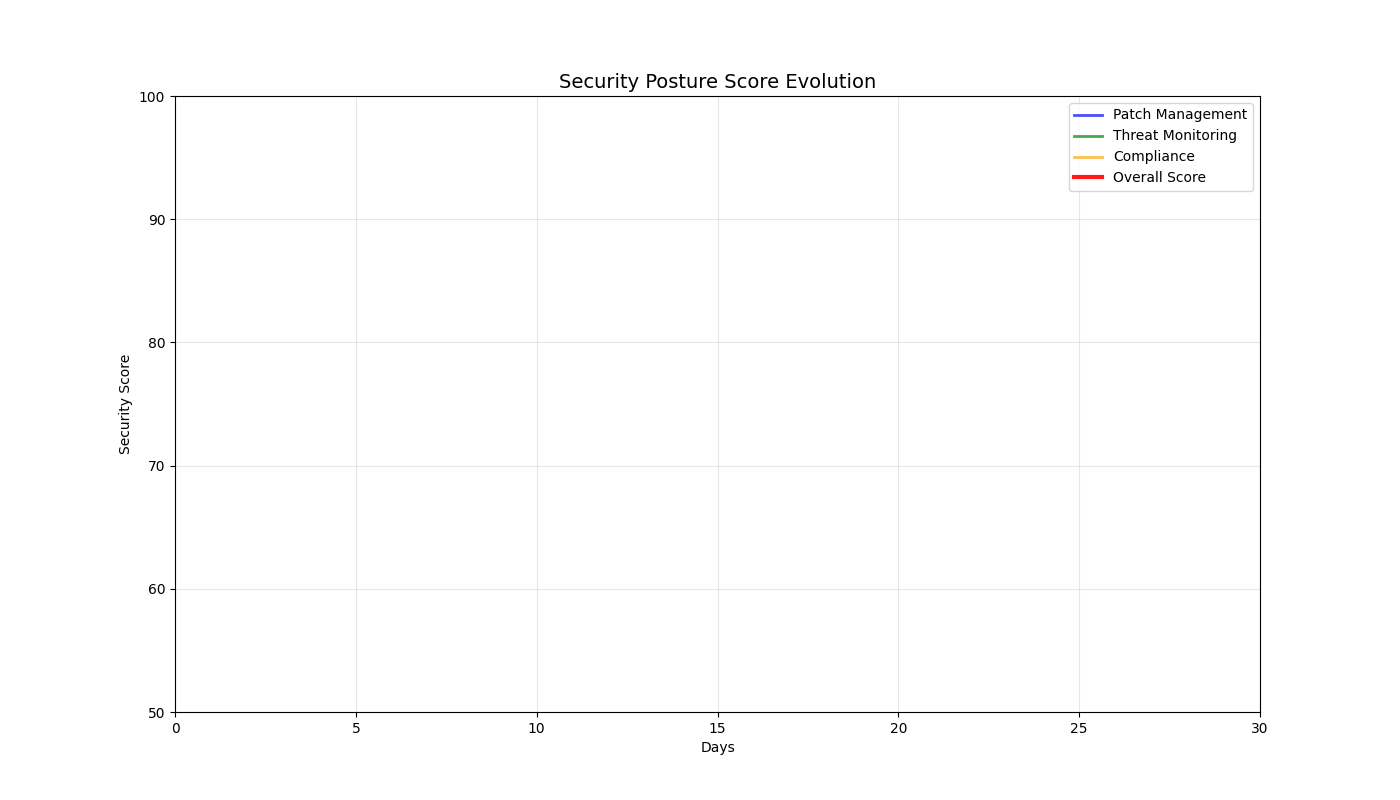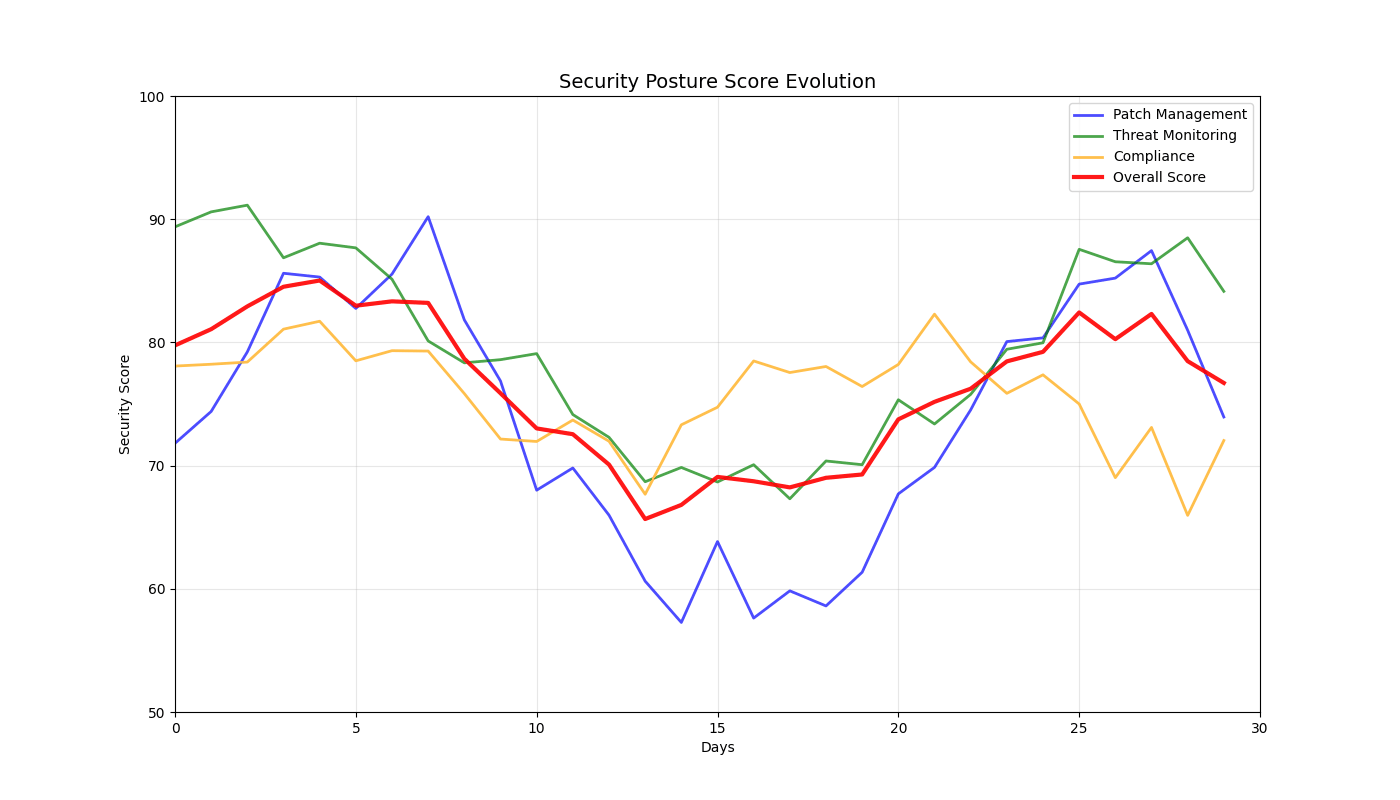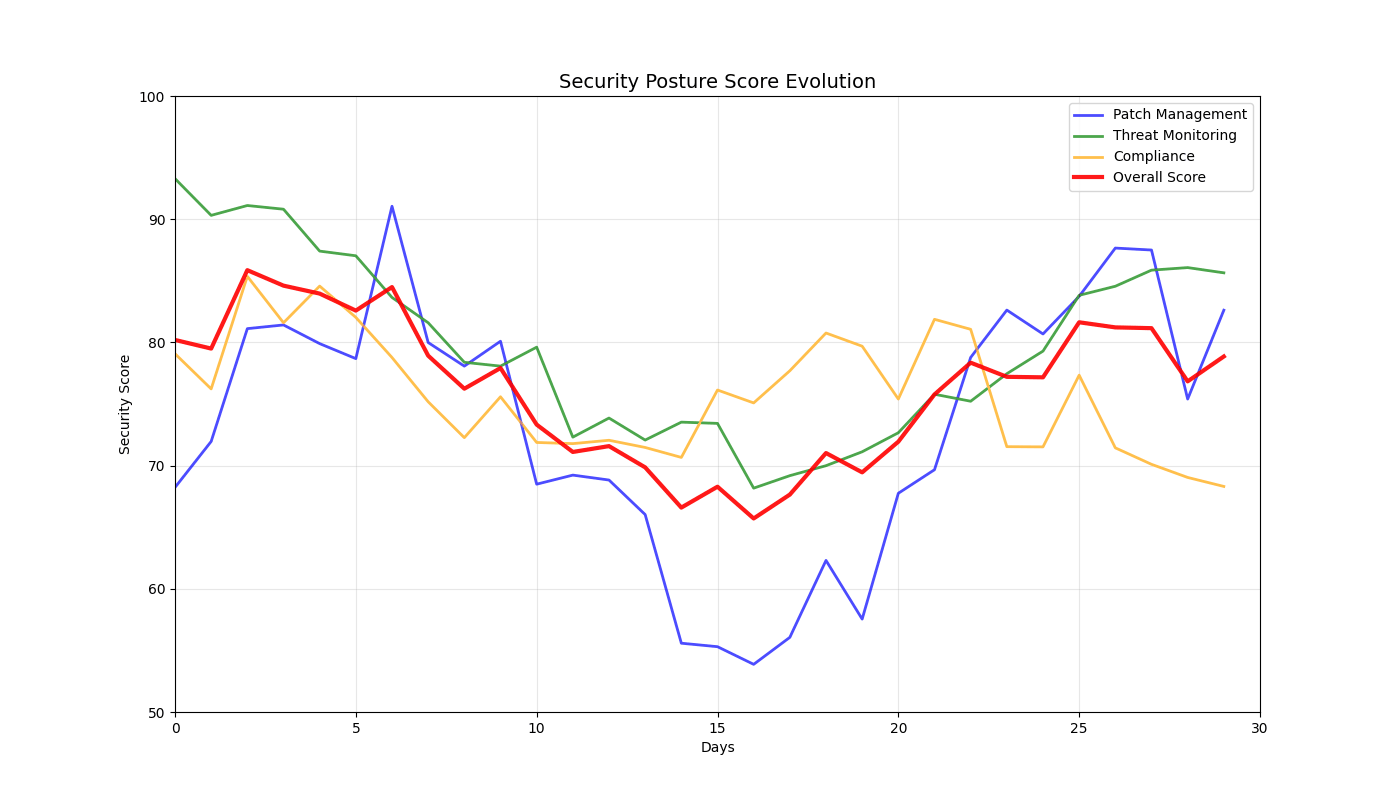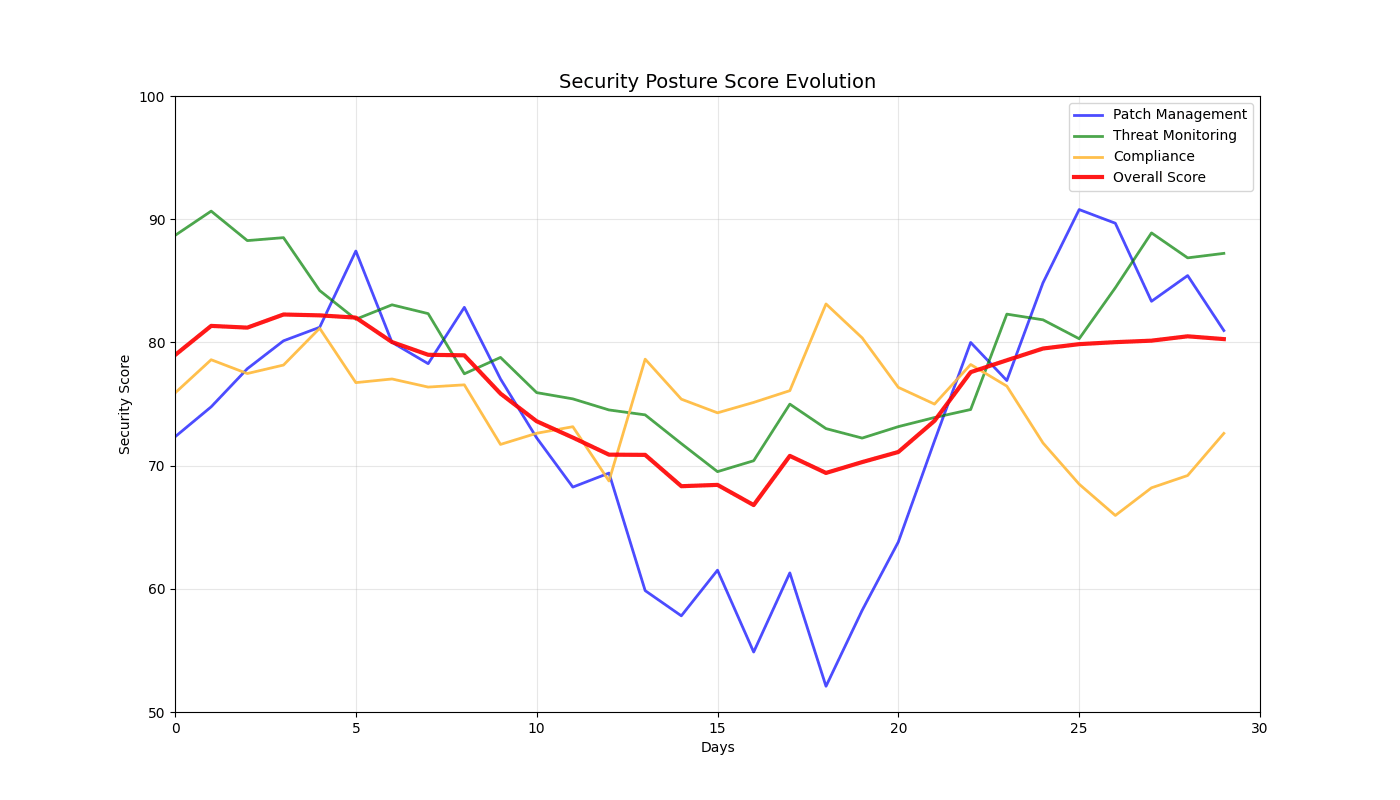
Real-time 3D/2D visualizations of threat landscapes, attack patterns, network security posture evolution, and incident response optimization.
3D Threat Visualizations
2D Security Analytics
Threat Intelligence Dashboard
Comprehensive cybersecurity dashboard with attack distribution, severity breakdown, risk scoring, quantum threat states, and detection metrics.
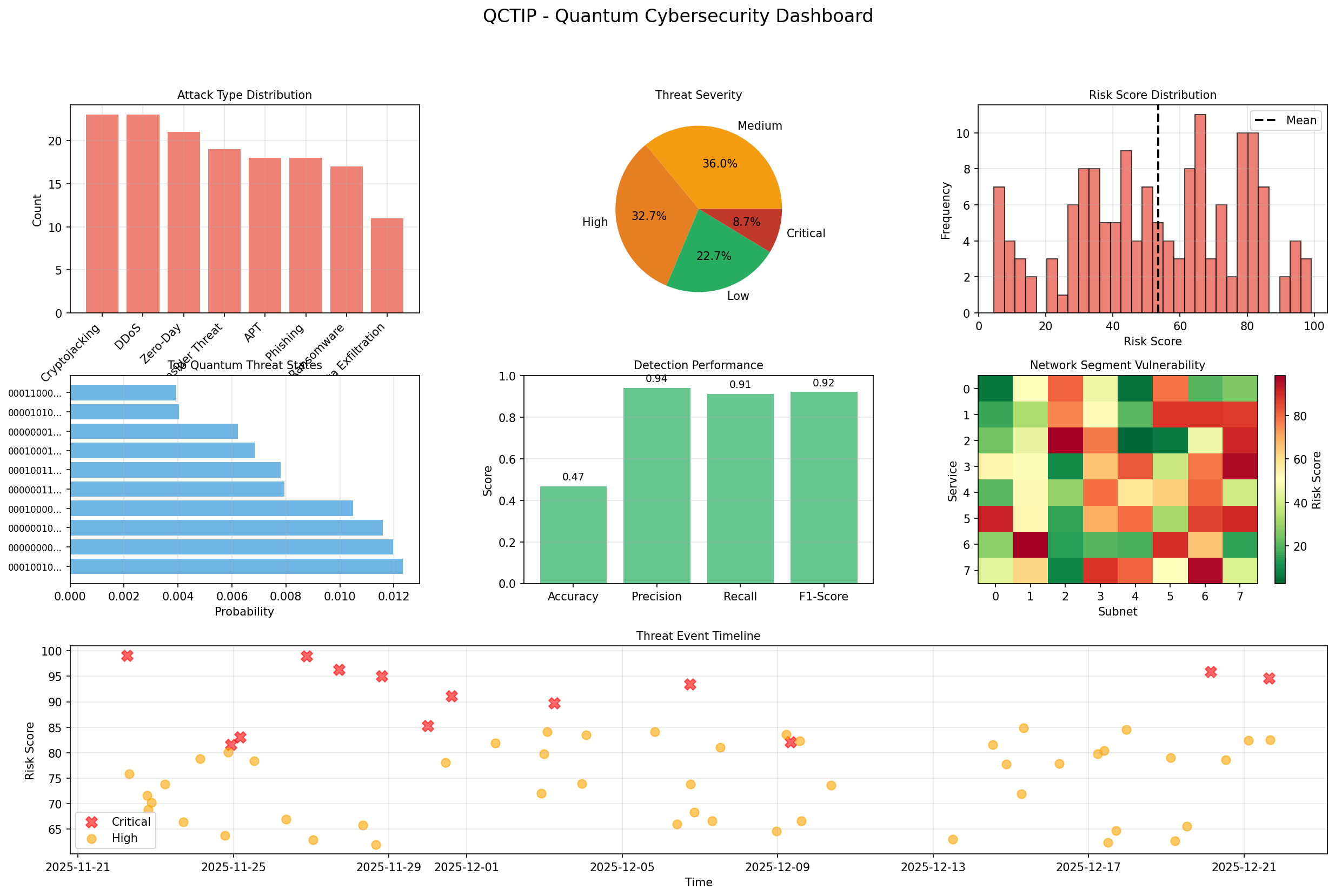
The dashboard includes attack type distribution, threat severity pie charts, risk score histograms, top quantum threat states, detection performance metrics, network vulnerability heatmaps, and real-time threat event timelines.
Generated Output Files
Complete set of analysis outputs including interactive reports, simulation files, dashboards, and structured data exports.
Source Code & Integration
Complete Python implementation with quantum circuit builder, threat analyzers, and visualization generators. Fully open-source and production-ready.
SIEM Integration
API connectors for Splunk, Elastic Security, Chronicle, and QRadar
Threat Intel Feeds
MISP, STIX/TAXII, OpenCTI, and custom IOC ingestion